I'm trying to make a server/client communication with a lwm2m server and DTLS authentification.
In the first place, I used Pre Shared Key that i provided with the modem key management library which work very well.
But now i want to use DTLS with certificate. However, as you can see, there is no credential type corresponding to client certificate.
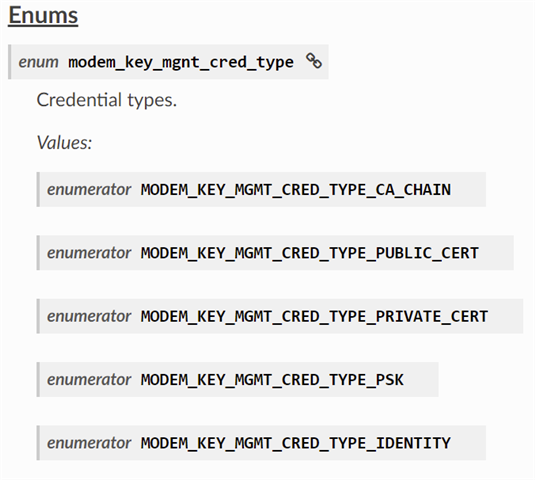
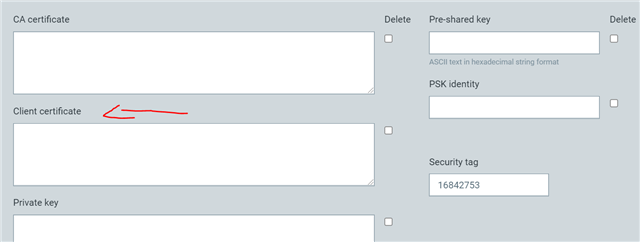
I'd like to know how i can provide a client certificate for a mutual authentification (hard coded)


