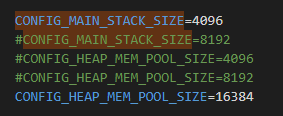
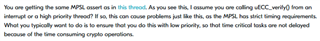
Hello,
I am developing FW for a BLE Peripheral on NRF52840_DK using nRF Connect SDK v1.9.1 on VScode.
So far, Peripheral and Client are able to connect and exchange data.
When Client is sending data: with a digital signature (raw 65 bytes) and its public key (raw, 65 bytes), In the Peripheral Code,
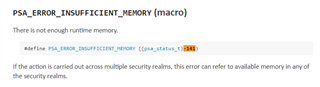
I need help in implementing digital signature using PSA library using psa_verify_message() function.
So far, i have used these functions successfully :
psa_crypto_init()
psa_generate_random()