Hi ,
I have compiled in Heart rat relay into my app; can scan and connect to simulator and garmin HR straps; but fail to connect to polar.
My debug log shows...
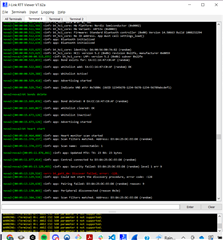
So security is encryption, no auth and I get an "unspecified" error.
I have done a BLE wireshark trace; but cannot see anything in the trace to indicate the issue.
Would be grateful if someon could look and give me a clue to whats going wrong.
Here is wireshark trace....
polarHrmActiveScanConnectFail.pcapng
Regards,
Owain


