Hi there,
I am wondering could the nRF sniffer follow a connection of two nRF Connect SDK built applications?
What I got is like the following:
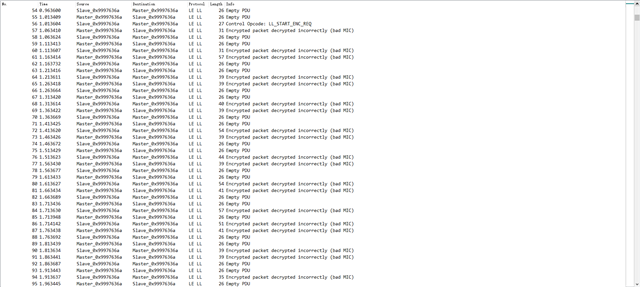
After some searching in the DevZone, I followed their advice but still got into this "bad MIC" case.
I already sniffed the whole process from the beginning (including CONNECT_IND).
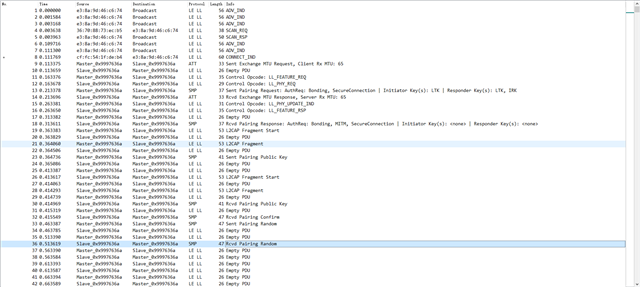
Hence, indeed, could the nRF sniffer detect and follow nRF Connect SDK applications?
Really appreciate it if this could be answered ASAP.
Best regards :-)
Ethan


