hello,
I use download sample on nRF9160DK with NCS2.0. I tried to change the SAMPLE_FILE_URL to my server URL, and the certificate was also modified, my configuration is as follow.
CONFIG_NRF_MODEM_LIB=y CONFIG_NETWORKING=y CONFIG_NET_SOCKETS=y CONFIG_NET_NATIVE=n CONFIG_HEAP_MEM_POOL_SIZE=1024 CONFIG_MAIN_STACK_SIZE=2048 CONFIG_MODEM_KEY_MGMT=y CONFIG_LTE_LINK_CONTROL=y CONFIG_LTE_AUTO_INIT_AND_CONNECT=n CONFIG_DOWNLOAD_CLIENT=y CONFIG_NEWLIB_LIBC=y CONFIG_LTE_NETWORK_MODE_NBIOT=y CONFIG_COAP=y CONFIG_SAMPLE_SECURE_SOCKET=y CONFIG_LOG_PRINTK=y CONFIG_LOG=y
However, the connection to the server was rejected.
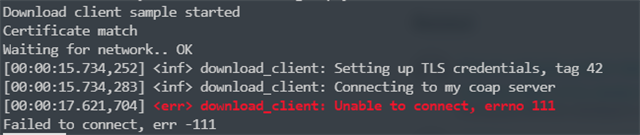
I know that this sample supports COAP and DTLS, this is explained in the documentation:
But I could never achieve it.
Thanks!
