I am attempting to connect a nRF52840dk to Azure IoT Hub using OpenThread and TCP. I combined the azure_iot_hub and azure_fota samples into one project, which ran successfully on an nRF9160dk using Connect SDK v1.9.1. I have modified that project for a nRF52840dk, OpenThread, TCP, and Connect SDK 2.0.0. I think that I am close, but I am getting error -22 ("invalid argument") in azure_iot_hub.c's mqtt_connect().
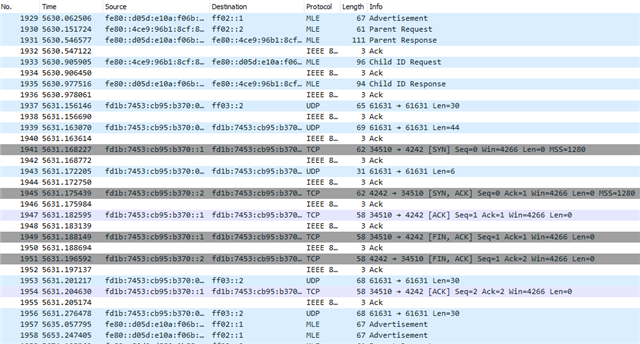
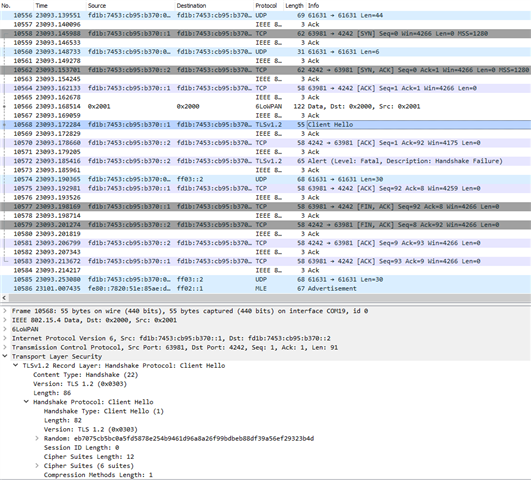
Wireshark capture using nRF sniffer:
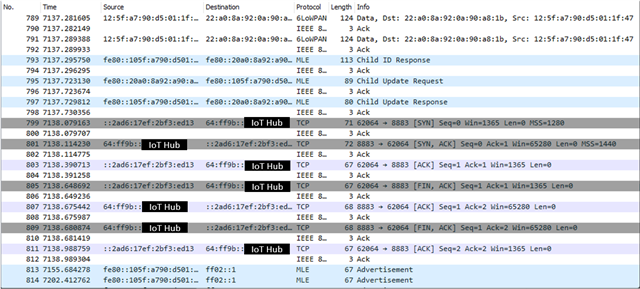
Serial output (I added the "Error in zsock_connect!" log in mqtt_transport_socket_tls.c):
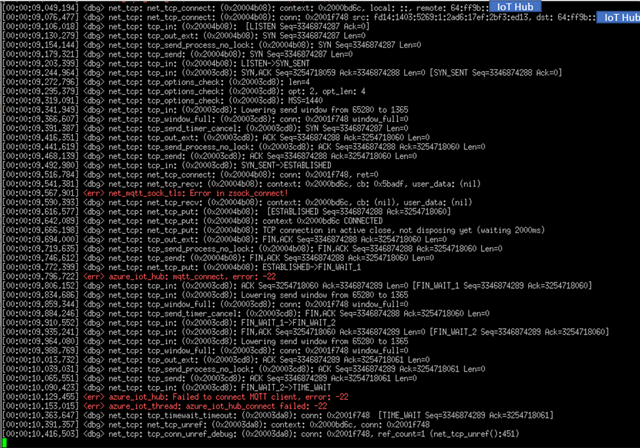
I've repurposed CONFIG_AZURE_IOT_HUB_STATIC_IPV4 to be an ipv6 address as seen in my prj further below. The getaddrinfo() DNS resolver is working, but I'd have to add a conversion from the returned ipv4 to ipv6 and I'd prefer to bypass that for now unless this is causing the issue. In azure_iot_hub.c's broket_init(), I changed &broker to &broker4 to resolve an error and made some other updates to switch from ipv4 to ipv6. These are the only changes I made in azure_iot_hub.c. The IoT Hub setup is kicked off in main() via err = azure_iot_hub_connect();
prj.conf:
Certificate format:
Per this DevZone ticket and this Microsoft documentation, maybe I am missing something with the CBC ciphers and MBedTLS? TCP messages appear to be going back and forth between the IoT Hub MQTT and my OpenThread end device in the Wireshark sniffer trace, so hopefully I am close to the finish line. Thank you in advance for the assistance.