I have an Ellisys Bluetooth Explorer 400 sniffer and am trying to sniff the ISO audio data between nrf5340 ADK boards. I enabled CONFIG_BT_LOG_SNIFFER_INFO, CONFIG_BT_DEBUG_KEYS and CONFIG_BT_DEBUG_SMP. This allows me to see in the debug logs a bunch of the different keys used for establishing encryption. But it is hard to tell which is the Link Key, and, worse, my sniffer says it isn’t getting enough info over the air to even make use of the Link Key if I provided it. See the below screenshot.
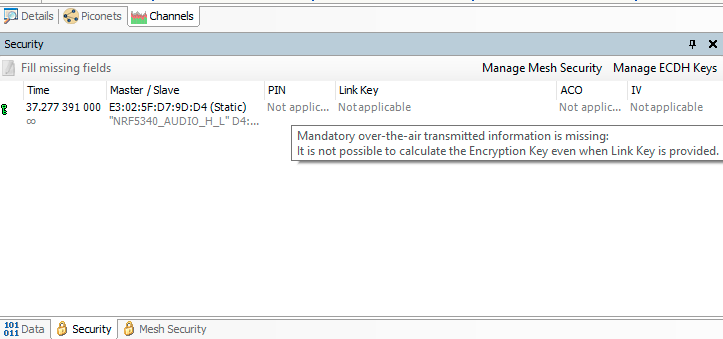
I’m surprised the ADK docs don’t seem to provide a simple “switch” or process for enabling sniffer decryption. Sniffing the traffic is a fundamental part of analysis and development. Am I missing something here?
Thanks,
Chris


