hello,
we are trying to use the stack guard module - obviously we want this to give well-behaved fault handling in the event that the stack gets too close for comfort.
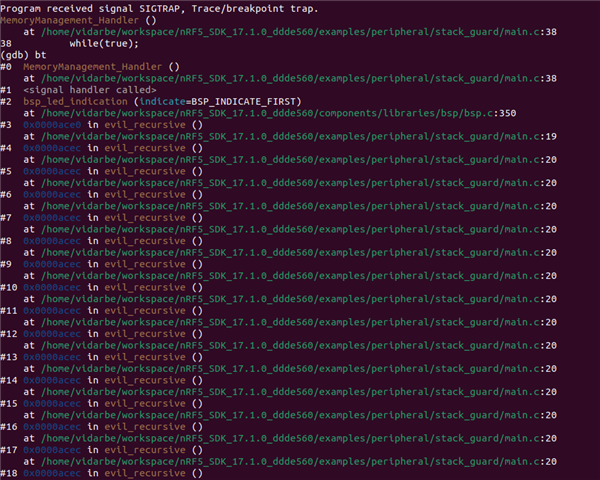
What we found when testing is that an explicit write to the guard area raises a Memory Manager Fault, as expected. However when we trigger a real stack overflow (by writing a recursive function that does not exit), we found the processor locking up.
I spent a bit of time to extract a "minimal example" from our prototype code, and I found similar behaviour - in the example code below, you will find that calling the recursive function raises a Hard Fault.
Here is my minimal example:
// minimal implementation to show stack guard issue#include <stdio.h>#include <stdint.h>#include <stdbool.h>#include <string.h>#include "nrf_mpu_lib.h"#include "nrf_stack_guard.h"static uint32_t count = 0;void trigger_stack_guard(void){ uint32_t * stack = (uint32_t *)0x2000E1FE; *stack = 0xDEADBEEF;}void evil_recursive(void){ count++; evil_recursive();}void HardFault_Handler(void){ while(true);}void MemoryManagement_Handler(void){ while(true);}int main(void){ nrf_mpu_lib_init(); nrf_stack_guard_init(); // enable Mem Fault Handler SCB->SHCSR |= SCB_SHCSR_MEMFAULTENA_Msk; // just write to the guard area trigger_stack_guard(); // really cause a stack overflow evil_recursive(); while(true);}
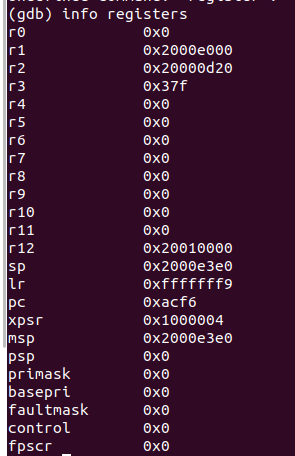
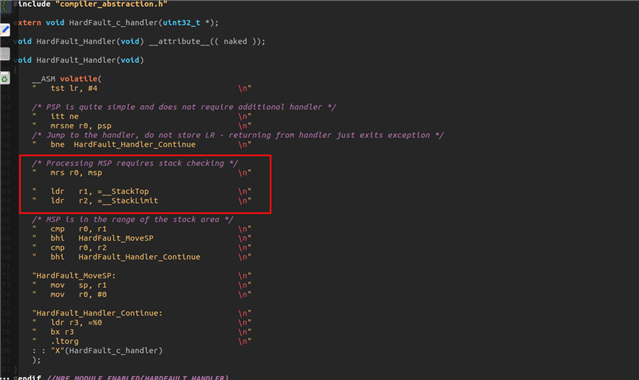
If you run this as is and connect gdb, you will get to the MemoryManagement_Handler as expected. However if you comment out the trigger_stack_guard() call and run the recursive function, you get Hard Fault Handler.
Not sure why this is - we would like to know why it doesn't work as expected.