I'm attempting to create an NFC type 4 message to allow certain information to be read using a phone or other NFC reader. I've studied a number of examples, but none that does exactly what I want, i.e. Type 4 text records. The nearest I've found is the writable_ndef_msg example, but this uses file-based records, which I don't need, and I can't see the proper way to create records programatically without using the filesystem.
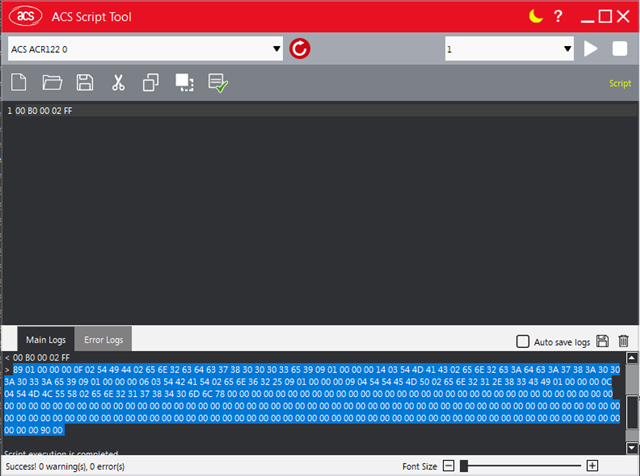
I've made some headway by scanning another known-good type 4 device using an ACR122 USB reader and a script tool to dump the raw data, and then I've crafted a packet that exactly matches this.
However, when I attempt to read using a phone I can't get any response at all.
I'm not an expert on NFC. I suspect that there's something in the preamble of the protocol (i.e. something that the NFC script tool doesn't show me) that's not right, but I can't see anything in the NFC API that would allow me to experiment.
I've included below the code I'm using, if you're able to offer any advice on what I should try or how I should be going about it, I would be most grateful to hear.
Cheers,
Frog