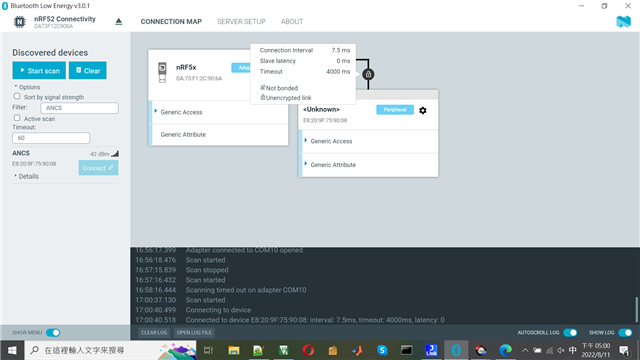
I use nRF Connect to connect to nRF52832 device. 1st connection is bonded authenticated encrypted link, but 2nd connection becomes not bonded unencrypted link. Why 1st and 2nd connection are different?
The following is log message of nRF52832 device.
00> <info> app: POWER_ON.
00> <debug> nrf_ble_gatt: Requesting to update ATT MTU to 185 bytes on connection 0x0.
00> <info> app: BLE_GAP_EVT_CONNECTED (1st connection)
00> <debug> app: state=1
00> <debug> nrf_ble_gatt: ATT MTU updated to 185 bytes on connection 0x0 (response).
00> <debug> app: _securityRequestHandler
00> <info> app: BLE_GAP_EVT_SEC_PARAMS_REQUEST
00> <info> app: PM_EVT_CONN_SEC_SUCCEEDED
00> <info> app: Connection secured: role: 1, conn_handle: 0x0, procedure: 1.
00> <debug> nrf_ble_gatt: Requesting to update ATT MTU to 185 bytes on connection 0x0.
00> <info> app: PM_EVT_BONDED_PEER_CONNECTED
00> <info> app: BLE_GAP_EVT_CONNECTED (2nd connection)
00> <debug> app: state=1
00> <debug> nrf_ble_gatt: ATT MTU updated to 185 bytes on connection 0x0 (response).