Target nRF52832(nrf52dk_nrf52832)
SDK NCS v2.0.0
I'm testing NCS 2.0 with Android 12.
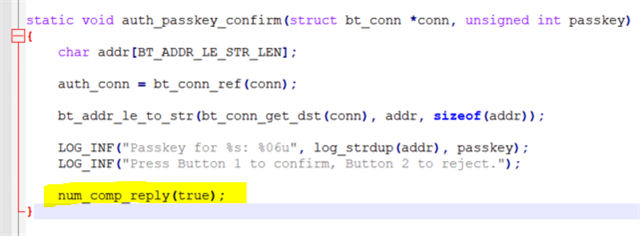
Making pairing with Android, I call two API when connected.
bt_set_bondable(true);
bt_conn_set_security(conn, BT_SECURITY_L4);
It worked well so far (under Android 11)
BTW Android 12 make trouble security level 1 error.
[log]
00> HS connected
00> HS Connected 4A:B4:CA:22:85:2D (random)
00> Connection parameters updated.
00> interval: 6, latency: 0, timeout: 500
00> Conn params updated: interval 7 ms, latency 0, timeout: 5000 ms
00> Security failed: 4A:B4:CA:22:85:2D (random) level 1 err 2
00> Disconnected: 4A:B4:CA:22:85:2D (random) (reason 34)
Can I have another option to make pairing automatically?