Hello,
after upgrading to SDK15 and using the new crypto functionality I experience some weird behaviour during bonding.
Our SW is the peripheral and I am starting the Bonding by trying to read a protected characterisitc with the nrfConnect App on Android.
After exchanging Public Keys the Master(Android App) aborts with a DHKey Check failed.
This is the code i use to generate the public key
/* Init nrf_crypto and the RNG */
err_code = ble_lesc_init();
APP_ERROR_CHECK(err_code);
/* Generate the ECDH key pair and set public key in the peer-manager. */
err_code = ble_lesc_ecc_keypair_generate_and_set();
APP_ERROR_CHECK(err_code);
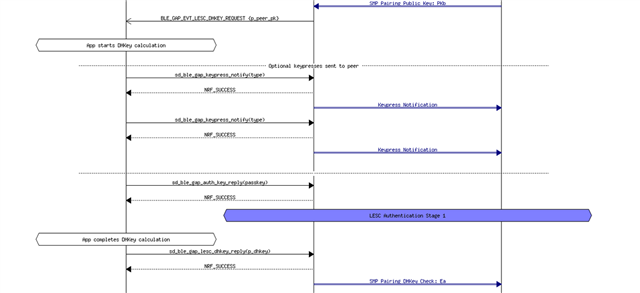
On our peripheral i receive BLE_GAP_EVT_LESC_DHKEY_REQUEST and start ble_lesc_service_request_handler().
It correctly calls ble_lesc_dhkey_calculate_and_set() and I can see that sd_ble_gap_lesc_dhkey_reply() returns success.
But then I receive the abort from the peer device. I am not sure what can go wrong with the public key on the nRFConnect side. I added the procedure and the public keys below.
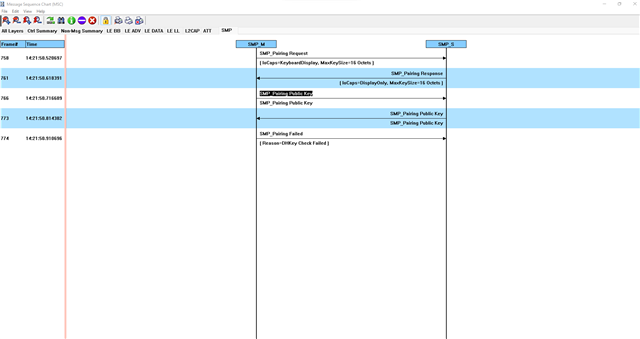
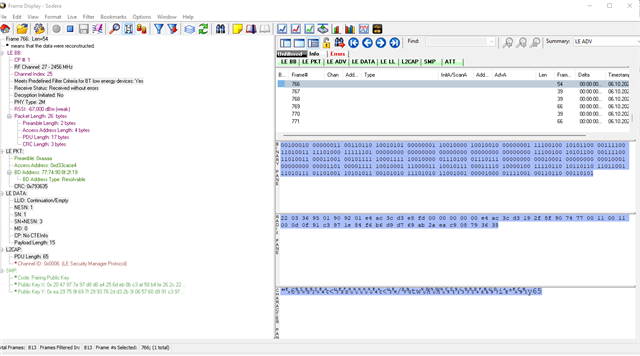
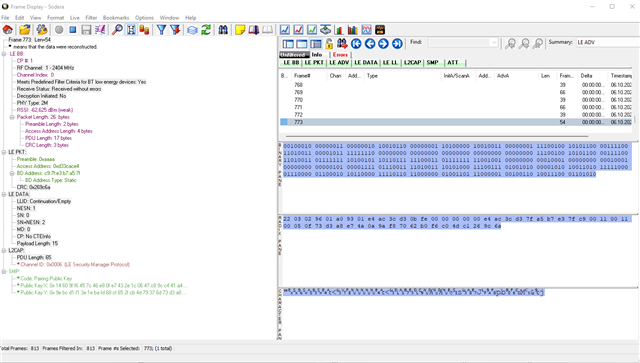
We are using NRF52840_XXAA with SoftDevice S140 v6.0.0 and SDK 15.0
If you could provide any insight on why this could happen i would greatly appreciate it.
Best regards,
Niclas