Hi,
I'm using the following function in my project, in order to get an idea of how much memory can be reserved with malloc:
static uint32_t GetFreeMemorySize()
{
uint32_t i;
uint32_t len;
uint8_t* ptr;
for(i=1;;i++)
{
len = i * 1024;
ptr = (uint8_t*)malloc(len);
if(!ptr){
break;
}
free(ptr);
}
return i;
}
This function should return the last value of i that was tested.
When I use it from the main.c of my application (from the non-secure partition), it works correctly. However, if I launch it inside my secure partition (TF-M), the function works correctly until before the last malloc. But, in this last malloc, instead of failing and terminating the function, the board reboots.
I don't know if there is a default setting that causes a failed malloc to restart the board, but I would like this not to happen, and get the return value of i.
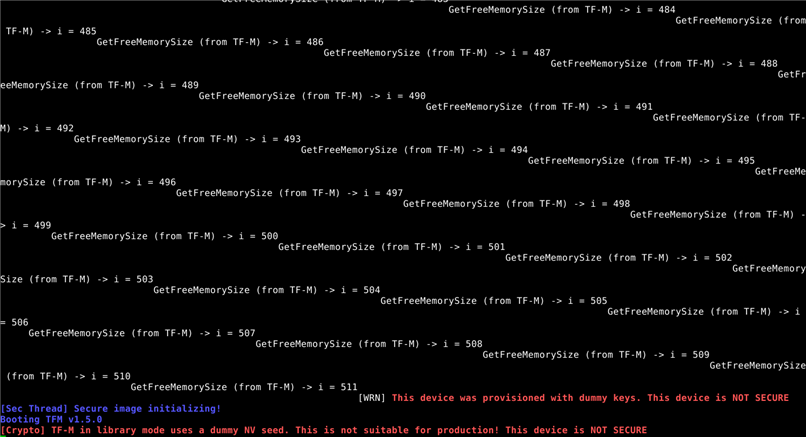
I know that the function runs inside my safe partition. I have verified this by adding a printf inside the function and observing the output of TF-M, as can be seen below:
static uint32_t GetFreeMemorySize()
{
uint32_t i;
uint32_t len;
uint8_t* ptr;
for(i=1;;i++)
{
len = i * 1024;
ptr = (uint8_t*)malloc(len);
if(!ptr){
break;
}
free(ptr);
printf("GetFreeMemorySize (from SPM) -> i = %d\n", i);
}
return i;
}
Regards,
Pablo
Useful information about the project:
- I'm using the nRF5340DK development kit.
- nRF Connect SDK v2.0.0
- The project is based on the example: TF-M Secure Partition Sample.