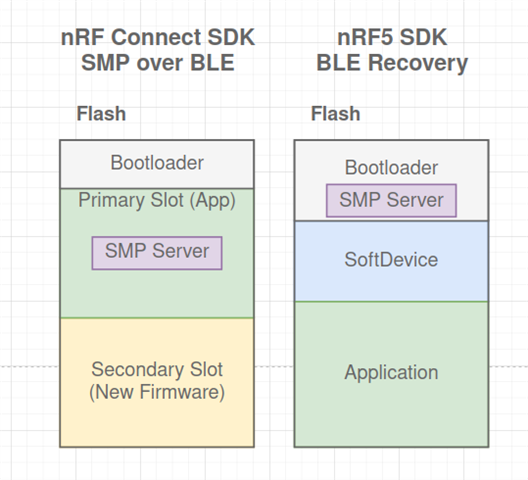
I am trying to make a recovery image for my app that allows me to press a button on power-up to recover a possibly bad update over BLE.
If an update is sent to a device that has a critical error that prevents the SMP SVR from running or BLE devices from connecting, I would like to be able to boot into a recovery mode that allows a new update to fix the device.
With the NRF5 SDK, I could do this easily since the DFU image ran separate from the app.
I do not have access to a uart so I cannot use the MCUboot recovery.
My issue is like this case, but I do not see a solution here:
devzone.nordicsemi.com/.../make-mcuboot-select-recovery-app
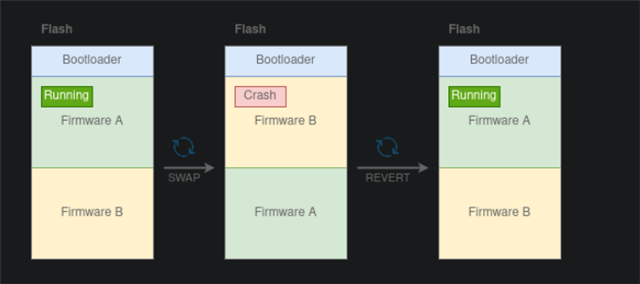
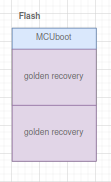
I was thinking I could use the CONFIG_BOOT_UPGRADE_ONLY setting to keep MCU Boot from using Slot1. Then use slot1 for the recovery image?
I could either:
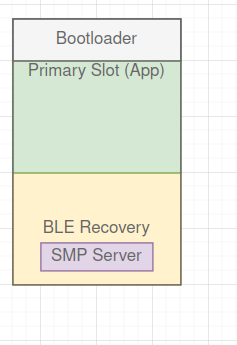
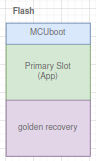
- Swap golden recovery image:
Keep a working, tested copy in Slot1 and copy this to Slot0 when recovery mode is activated. - Make a minimal build of the SMP SVR BLE for the recovery image.
This would be nice as I would have more space for the app.
+-------------------+ | MCU Boot | +-------------------+ | App (slot0) | +-------------------+ | Recovery (slot1) | +-------------------+
Questions:
- I believe I need to set up the recovery image as a child image correct? Any examples to look at on how to do this?
- Perhaps I can just specify a hex file for the recovery image if doing approach number1?
- Can I make a customer recovery child image with a minimal SMP SVR BLE build that can update slot0?
- Any recommendations on either of these approaches or a different approach?
- My biggest concern is how to setup the partitions for this.