Hi all,
This is for nrf9160 with firmware version 1.3.1.
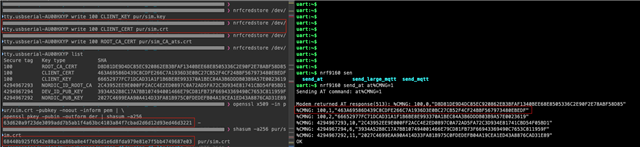
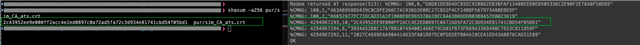
I 'm trying to read back the certificates and comparing with a known CRC.
modem_key_mgmt_read is able to read the CA_CHAIN cert, but cannot read the Public_Cert and the Private_Cert. (retruns FFs, length = 0)
Is that for obvious security reasons that you wouldn't be able to read those certs?
If so, is there a way for getting a length or a checksum of each of the fields, to verify that the contents in NV memory are valid?
I have used the modem_key_mgmt_cmp after the write new values to confirm the values are the same as those written and that works for all the above three certificates.
Best regards,