Information about my setup:
I'm working on a product using nRF52832 with SDK 17.0.2 and Softdevice s132 7.2.0. It is a custom board.
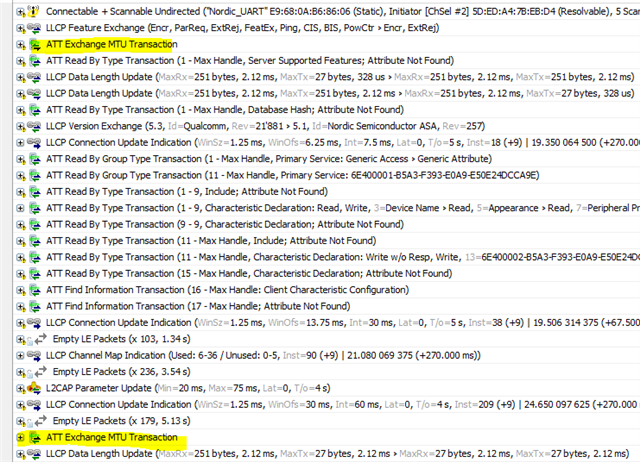
The default configuration (peripheral side - nRF52832) negotiate BLE connection parameters as follows:
- MTU: 230 Bytes
- Data Lenght: 234 Bytes (NRF_SDH_BLE_GAP_DATA_LENGTH)
- NRF_SDH_BLE_GAP_EVENT_LENGTH: 10 (1.25 ms units)
- PHY: 2 MB
- MIN_CONN_INTERVAL: 150 ms
- MAX_CONN_INTERVAL: 180 ms
- SLAVE_LATENCY: 5
- CONN_SUP_TIMEOUT: 4000 ms
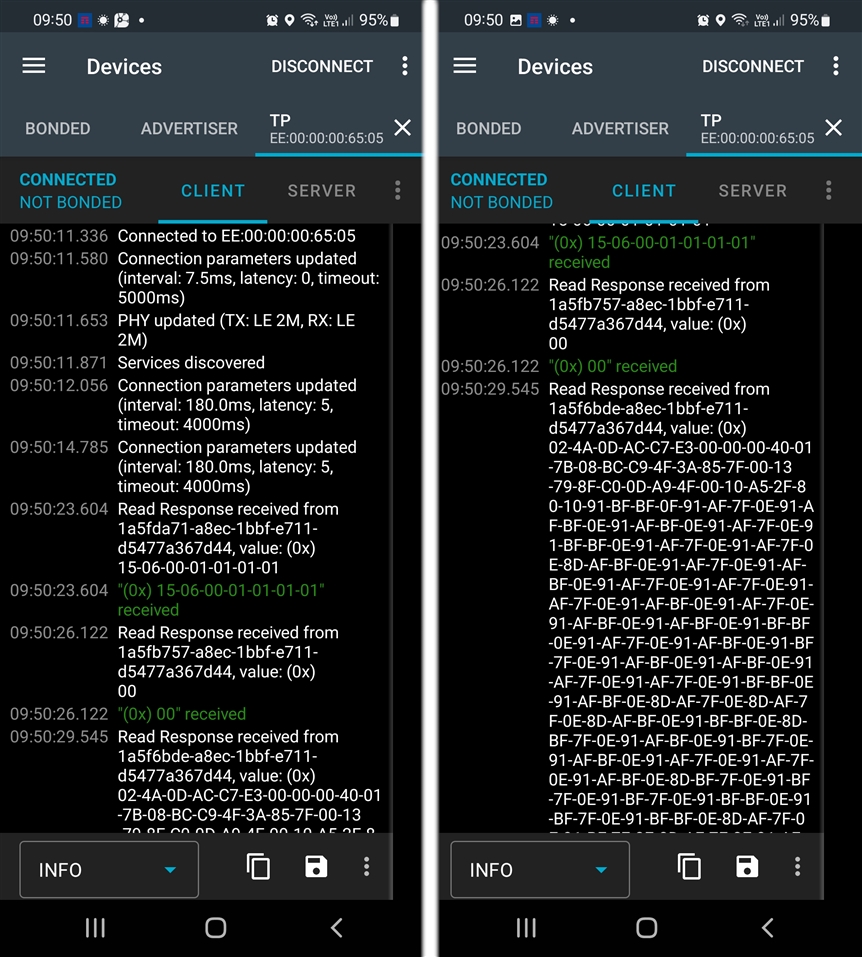
The device (nRF52832) have a custom service with multiple characteristics. Some of these characteristics can have up to 512 bytes of data available to read. The Nordic nRF Connect Android APP is used for test purposes and the reading of characteristics is performed using the "down arrow" read button available in the APP next to all characteristics configured as "read enabled". A few recent smartphone models from different brands were used in tests, all with the same results.
Normal Behavior:
When the device connects to a smartphone, the parameter negotiation ends smoothly within the specified parameters. All readable characteristics in the custom service can be read with no problems.
Problem situation:
Multiple tests are performed to confirm proper device operation in various use cases. One of the tests requires renegotiating some of the above parameters after the connection is stablished.
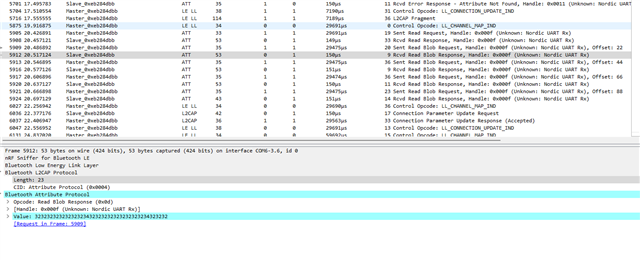
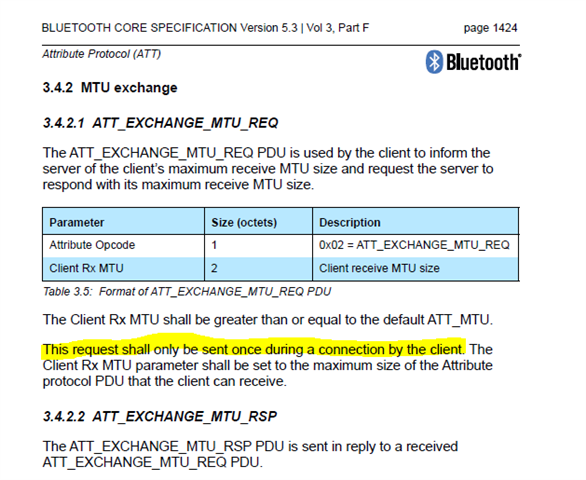
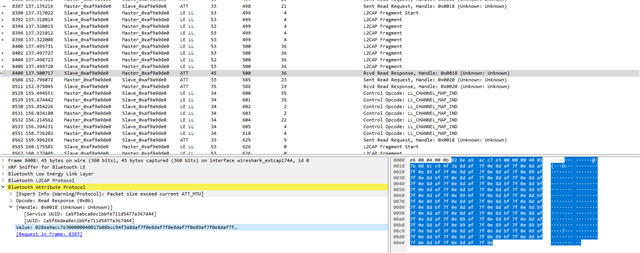
The problem starts when the MTU is changed to 23 (regardless of other parameters). The negotiation of the MTU itself finishes successfully. After that, only characteristics with few bytes of data can be read. If you try to read longer characteristics a GATT 133 error is reported in the nRF Connect side and the data is not received. The nRF52832 appears to believe the data has been sent and updates the data for new readings.
The connection is not lost after GATT 133 error, it remains stable and other characteristics can be read. If the characteristics are larger than a certain amount of bytes a new GATT 133 error is reported, otherwise the data is correctly received by nRF Connect.
Is there some configuration or something that could be preventing more than a few bytes of data from being read from a characteristic when the smartphone negotiates a 23 bytes MTU?
Is there any way (or any reading mode of BLE characteristics) to automatically confirm that data has been received by the smartphone on the nRF52832? Some of the data must be erased from the device after the smartphone reads it, it would be nice to have confirmation of data delivery in the lower layers of the BLE/SDK to avoid this kind of management in my code.
Thank you in advance for your help.