I am using nrf5340dk board and trying to import a key using PSA API. The api used is psa_import_key() API for key attributes,
key_id = 0x010001A0, key_type = PSA_KEY_TYPE_AES , key_bits = 128, key_usage = PSA_KEY_USAGE_DERIVE, key_alg = PSA_ALG_CMAC
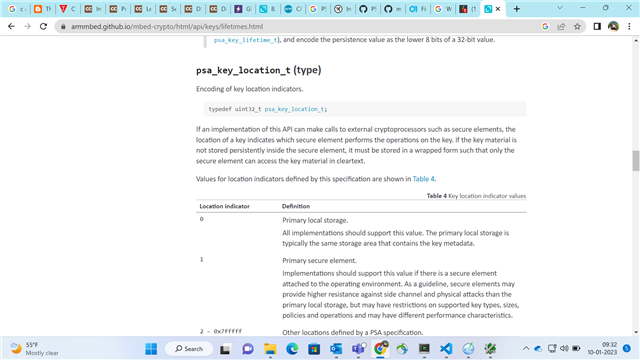
key_lifetime = 0x00000101 ( Persistence level -> PSA_KEY_PERSISTENCE_DEFAULT, Location indicator -> Primary secure element )
PSA spec says, Implementations should support Primary secure element(location indicator)
value if there is a secure element attached to the operating environment. As a guideline,
secure elements may provide higher resistance against side channel and physical attacks
than the primary local storage, but may have restrictions on supported key types, sizes,
policies and operations and may have different performance characteristics.
If I use Primary local element which means as per PSA spec, primary local storage is typically the same storage area that contains the key metadata instead of Primary secure element , key import works.
I would like to know if there is any restriction from hardware i.e. Primary secure element to store above specified type of key.