Hi All,
I am currently working on establishing a thread network to communicate to our http server:https://mainnet.incubed.net). In order to setting up that I took echo_client and http_client sample and adapted to our need. Below diagram is my network configuration with RPi connected with ethernet.
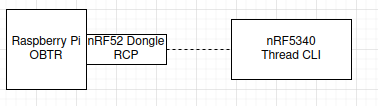
I was successful in pinging the http server from thread network. Here I wanted to send TCP packets to remote server via OT network.
I am novice to networking topics so it is really hard for me to understand and interpret the logs from the thread device. Below given is the log from the one node:
[00:00:00.396,331] <inf> ieee802154_nrf5: nRF5 802154 radio initialized [00:00:00.396,728] <dbg> net_tcp: net_tcp_init: (main): Workq started. Thread ID: 0x20008378 [00:00:00.411,651] <inf> fs_nvs: 2 Sectors of 4096 bytes [00:00:00.411,682] <inf> fs_nvs: alloc wra: 0, fe8 [00:00:00.411,682] <inf> fs_nvs: data wra: 0, 0 [00:00:00.412,994] <inf> net_l2_openthread: State changed! Flags: 0x00038200 Current role: disabled [00:00:00.418,487] <inf> net_config: Initializing network [00:00:00.418,487] <inf> net_config: Waiting interface 1 (0x20000a08) to be up... [00:00:30.419,189] <err> net_config: Timeout while waiting network interface [00:00:30.419,219] <err> net_config: Network initialization failed (-115) [00:00:30.419,525] <inf> in3_ot: Waiting for host to be ready to communicate [00:00:30.423,675] <inf> usb_cdc_acm: Device suspended [00:00:30.621,520] <inf> usb_cdc_acm: Device resumed [00:00:30.737,701] <inf> usb_cdc_acm: Device suspended [00:00:30.945,312] <inf> usb_cdc_acm: Device resumed [00:00:31.006,927] <inf> usb_cdc_acm: Device configured [00:00:44.243,072] <inf> net_l2_openthread: State changed! Flags: 0x00004000 Current role: disabled [00:00:44.243,713] <inf> net_l2_openthread: State changed! Flags: 0x00020000 Current role: disabled [00:00:44.243,804] <inf> net_l2_openthread: State changed! Flags: 0x00040000 Current role: disabled [00:00:44.243,896] <inf> net_l2_openthread: State changed! Flags: 0x00000100 Current role: disabled [00:00:44.247,131] <inf> net_l2_openthread: State changed! Flags: 0x00010000 Current role: disabled [00:00:44.247,222] <inf> net_l2_openthread: State changed! Flags: 0x00008000 Current role: disabled [00:00:44.247,741] <inf> net_l2_openthread: State changed! Flags: 0x10000000 Current role: disabled [00:00:44.247,985] <inf> net_l2_openthread: State changed! Flags: 0x10000000 Current role: disabled [00:00:44.249,053] <inf> net_l2_openthread: State changed! Flags: 0x00001000 Current role: disabled [00:00:44.249,237] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:44.249,267] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:44.249,389] <inf> net_l2_openthread: State changed! Flags: 0x00000001 Current role: disabled [00:00:44.249,450] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:44.249,542] <inf> net_l2_openthread: State changed! Flags: 0x00000008 Current role: disabled [00:00:44.249,664] <inf> net_l2_openthread: State changed! Flags: 0x01000000 Current role: disabled [00:00:44.249,786] <inf> net_l2_openthread: State changed! Flags: 0x00000004 Current role: detached [00:00:44.249,938] <inf> net_l2_openthread: State changed! Flags: 0x00000001 Current role: detached [00:00:44.250,030] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:44.250,152] <inf> net_l2_openthread: State changed! Flags: 0x00001000 Current role: detached [00:00:44.250,274] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:44.250,396] <inf> net_l2_openthread: State changed! Flags: 0x00001000 Current role: detached [00:00:44.250,549] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:44.250,640] <inf> net_l2_openthread: State changed! Flags: 0x00000010 Current role: detached [00:00:44.251,373] <inf> net_l2_openthread: State changed! Flags: 0x10000000 Current role: detached [00:00:46.497,467] <inf> net_l2_openthread: State changed! Flags: 0x200012a4 Current role: child [00:00:46.497,741] <inf> net_l2_openthread: State changed! Flags: 0x00000001 Current role: child [00:00:46.497,863] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:46.497,894] <wrn> net_l2_openthread: No address info provided with event, please enable CONFIG_NET_MGMT_EVENT_INFO [00:00:46.497,955] <dbg> in3_ot: ping_send: Ping Server: [00:00:46.497,985] <dbg> in3_ot: print_ipv6_address: Mesh Local EID Address: fd97.6739.093e.0002.0000.0000.a756.5ef8 [00:00:46.498,596] <dbg> in3_ot: ping_send: ping send response:0 [00:00:46.498,626] <dbg> main: main: Connected to thread network [00:00:46.499,145] <dbg> net_tcp: tcp_conn_ref: (main): conn: 0x20033d58, ref_count: 1 [00:00:46.499,176] <dbg> net_tcp: tcp_conn_alloc: (main): conn: 0x20033d58 [00:00:46.499,389] <dbg> net_tcp: net_tcp_connect: (main): context: 0x20013814, local: ::, remote: fd97:6739:93e:2::a756:5ef8 [00:00:46.499,542] <dbg> net_tcp: net_tcp_connect: (main): conn: 0x20033d58 src: fd11:22::271f:b127:ea60:6f99, dst: fd97:6739:93e:2::a756:5ef8 [00:00:46.499,664] <dbg> net_tcp: tcp_in: (main): [LISTEN Seq=1723021025 Ack=0] [00:00:46.499,938] <dbg> net_tcp: tcp_out_ext: (main): SYN Seq=1723021025 Len=0 [00:00:46.500,091] <dbg> net_tcp: tcp_send_process_no_lock: (main): SYN Seq=1723021025 Len=0 [00:00:46.500,305] <dbg> net_tcp: tcp_send: (main): SYN Seq=1723021025 Len=0 [00:00:46.500,671] <dbg> net_tcp: tcp_in: (main): LISTEN->SYN_SENT [00:00:46.567,230] <dbg> net_tcp: tcp_in: (rx_q[0]): ACK,RST Seq=0 Ack=1723021026 Len=0 [SYN_SENT Seq=1723021026 Ack=0] [00:00:46.567,260] <dbg> net_tcp: tcp_in: (rx_q[0]): SYN_SENT->CLOSED [00:00:46.567,352] <dbg> net_tcp: tcp_conn_unref_debug: (rx_q[0]): conn: 0x20033d58, ref_count=1 (tcp_in():2513) [00:00:46.567,382] <dbg> net_tcp: tcp_conn_unref_debug: (rx_q[0]): conn: 0x20033d58 is waiting on connect semaphore [00:00:46.573,516] <dbg> in3_ot: ping_reply_cb: Ping reply [00:00:46.573,547] <dbg> in3_ot: print_ipv6_address: Mesh Local EID Address: fd97.6739.093e.0002.0000.0000.a756.5ef8
Can someone tell me what is happening here and what I did wrong or not taken into my consideration.
Regards
Vipin Das
