We are writing certificates to our device correctly and they are functioning. However, on the assembly line we can't test the certificates right away. What I want to do is verify that the certs were written as expected before a device leaves the factory. (Understood that we can't check the private key but we should be able to hash our public certificate and root CA and check them)
I am using the AT%CMNG=1 to list out the certificates written. https://infocenter.nordicsemi.com/index.jsp?topic=%2Fref_at_commands%2FREF%2Fat_commands%2Fsecurity%2Fcmng.html
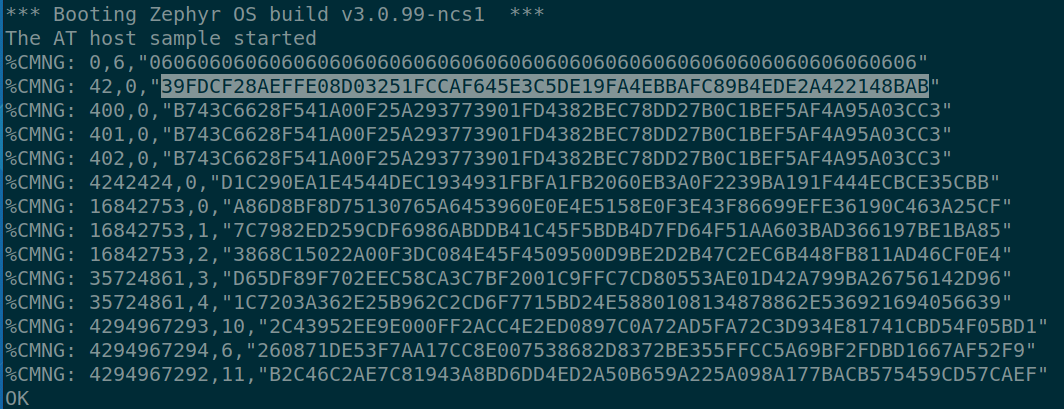
And it spits out a response like this:
AT%CMNG=1,12345678, 0
%CMNG: 12345678, 0, "978C...02C4"
OKFrom this ticket SHA-256 digest on %CMNG list credentials command looks strange see the response is a SHA-256 hash.
I ran a SHA-256 digest on the Root CA in PEM format written to the device and the hash did not match the hash returned.
What exactly is getting hashed for the yellow highlighted response? Is there a better way to validate that certificates were written correctly?