I am working on a project to build a custom BLE interface to a third-party peripheral device (a pool chlorinator / pump controller FWIW). I need to sniff the traffic between the third-party mobile app and the peripheral to reverse engineer the protocol and encryption type. However, when I sniff the connection process, there seems to be quite a lot of connection steps that are missing. In an effort to debug what's going on here, I've sniffed the connection from the nRF Connect mobile app (instead of the third-party app) to the peripheral, which successfully connects and retrieves a bunch of attributes. At least this way the encryption is taken out of the equation, as the nRF Connect app won't be able to negotiate the encryption (right?). It still seems like I'm not seeing all the packets.
Here's what I'm doing:
I'm using a nRF52840 dongle to sniff the BLE comms between the nRF Connect app on my phone, and the peripheral .
Using Wireshark, I have selected the particular peripheral device from the device list, and captured the traffic while I connect to the peripheral with the nRF Connect mobile app.
Here is what the comms look like in wireshark (I've filtered the empty packets):
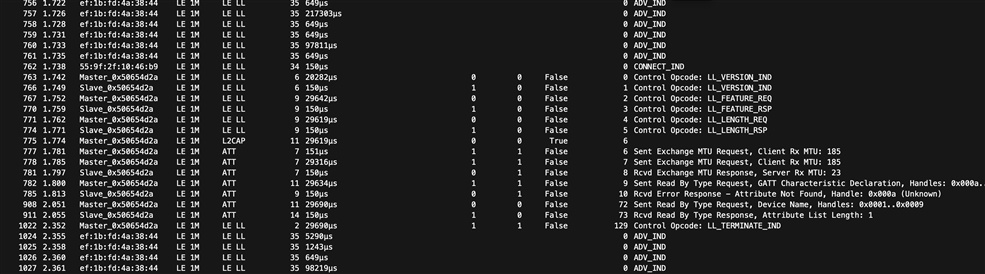
It appears that the sniffer is following the connection, but very little data is exchanged.
However, in nRF Connect, I get a long list of characteristics:
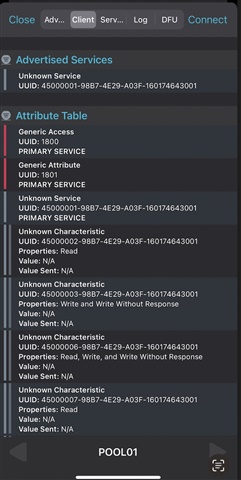
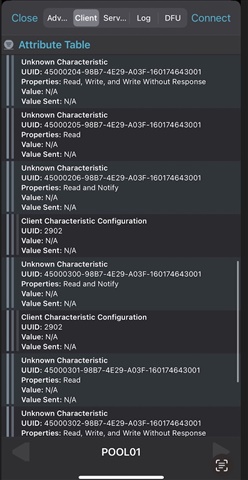
How does nRF Connect retrieve all these characteristics without seeing it in wireshark? Am I missing packets somehow?
Wireshark pcapng file
Chlorinator pairing new device.pcapng
Versions:
Sniffer firmware v4.1.1
Wireshark v4.0.3
MacOS v13.0.1
JLink v784f
MacOS VCP Driver v6

