Hey,
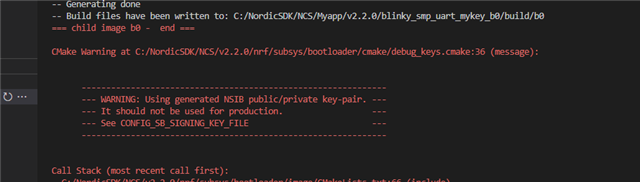
I'm trying to assign custom keys to the immutable nrf secure bootloader and to the updatable mcuboot, but without luck. I still get warning messages from both bootloaders regarding development keys still being used
snapshots of the prj.conf and mcuboot.conf
mcuboot.conf
CONFIG_BOOT_SIGNATURE_KEY_FILE="priv.pem" CONFIG_BOOT_ENCRYPT_RSA=n CONFIG_BOOT_SIGNATURE_TYPE_RSA=n CONFIG_BOOT_SIGNATURE_TYPE_ECDSA_P256=y CONFIG_MCUBOOT_DOWNGRADE_PREVENTION=y CONFIG_BOOT_UPGRADE_ONLY=y CONFIG_LOG=y CONFIG_LOG_MODE_MINIMAL=y CONFIG_FW_INFO_FIRMWARE_VERSION=8
prj.conf
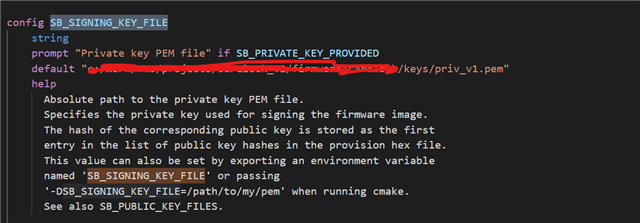
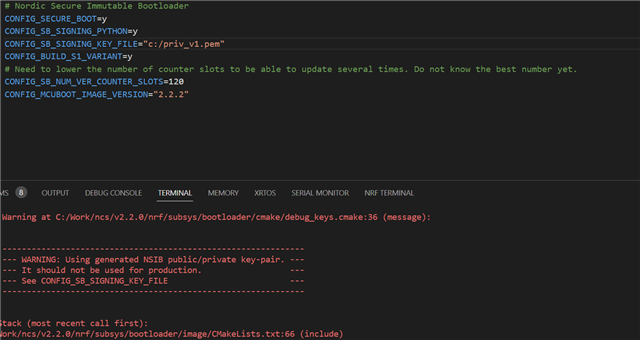
# DFU CONFIG_FW_INFO=y CONFIG_FW_INFO_FIRMWARE_VERSION=3 # mcuboot updatable Bootloader CONFIG_BOOTLOADER_MCUBOOT=y CONFIG_MCUMGR=y CONFIG_MCUMGR_SMP_BT=y CONFIG_MCUMGR_SMP_BT_AUTHEN=n CONFIG_MCUMGR_SMP_BT_CONN_PARAM_CONTROL=y CONFIG_MCUMGR_CMD_IMG_MGMT=y CONFIG_MCUMGR_CMD_OS_MGMT=y CONFIG_IMG_MANAGER=y CONFIG_MCUBOOT_IMG_MANAGER=y CONFIG_IMG_ERASE_PROGRESSIVELY=y CONFIG_NRF53_UPGRADE_NETWORK_CORE=y # # Enable statistics and statistic names. # CONFIG_STATS=y # CONFIG_STATS_NAMES=y # CONFIG_MCUMGR_CMD_STAT_MGMT=y # Enable MCUmgr Packet Reassembly feature over Bluetooth and its # configuration dependencies. MCUmgr buffer size is optimized to fit one SMP # packet divided into five Bluetooth Write Commands, transmitted with the # maximum possible MTU value: 498 bytes. CONFIG_MCUMGR_SMP_REASSEMBLY_BT=y CONFIG_MCUMGR_BUF_SIZE=2475 CONFIG_OS_MGMT_MCUMGR_PARAMS=y # Enable custom SMP request to erase settings partition. # CONFIG_MCUMGR_GRP_ZEPHYR_BASIC=y # CONFIG_MCUMGR_GRP_BASIC_CMD_STORAGE_ERASE=y # Nordic Secure Immutable Bootloader CONFIG_SECURE_BOOT=y CONFIG_SB_SIGNING_KEY_FILE="priv.pem" CONFIG_BUILD_S1_VARIANT=y # Need to lower the number of counter slots to be able to update several times. Do not know the best number yet. CONFIG_SB_NUM_VER_COUNTER_SLOTS=120 CONFIG_MCUBOOT_IMAGE_VERSION="2.2.2"
the project structure
my_project
- child_image
- mcuboot.conf
-priv.pem
- src
- prj.conf
- priv.pem
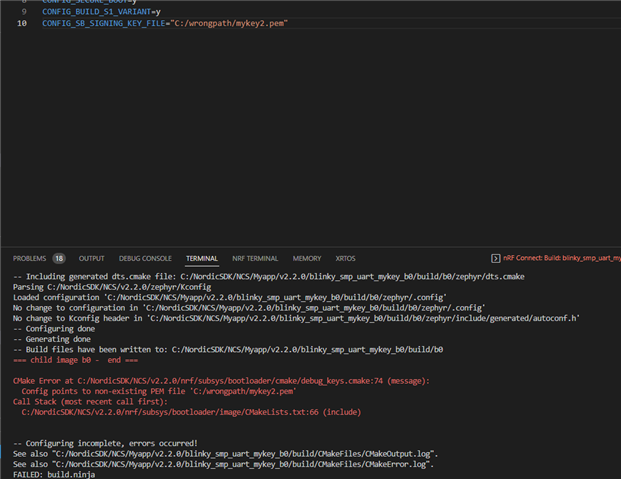
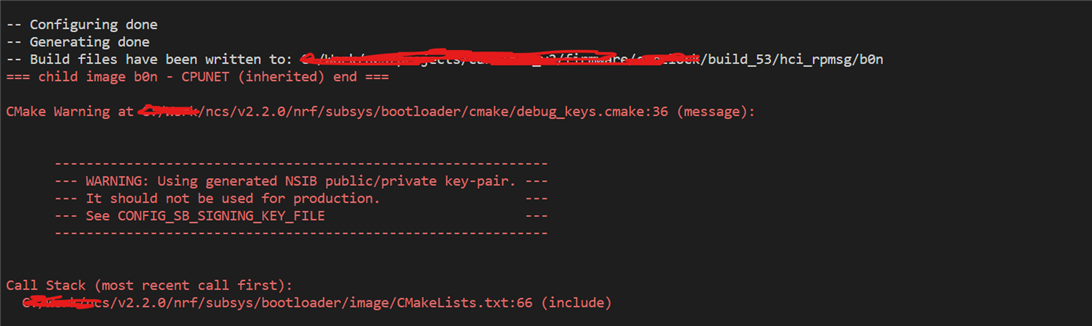
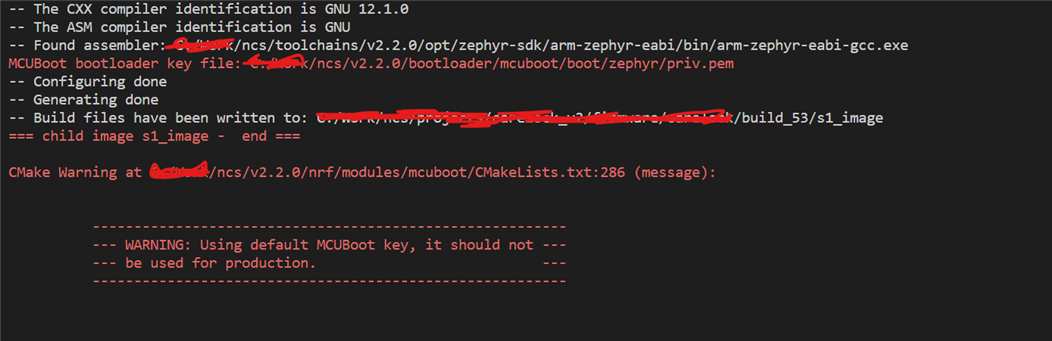
even I've tried to assign the key directly inside the bootloader/mcuboot/boot/zephyr/prj.conf but I got the same result even though the output log shows that priv.pem is used
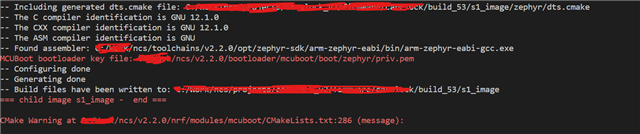
The key type is ecdsa-p256
updating the bootloader and the application works fine but still uses the development keys.
Could you please tell me what else I can do to solve this problem?
I really appreciate any help you can provide.
SDK; v2.2
soc: nrf5340