Hey Everyone,
Looking for some direction, I'm trying to create a secured DFU bond between my nRF52832 and the nRF Connect Mobile app following the instructions from the links below,
https://infocenter.nordicsemi.com/index.jsp?topic=%2Fsdk_nrf5_v17.0.2%2Fservice_dfu.html
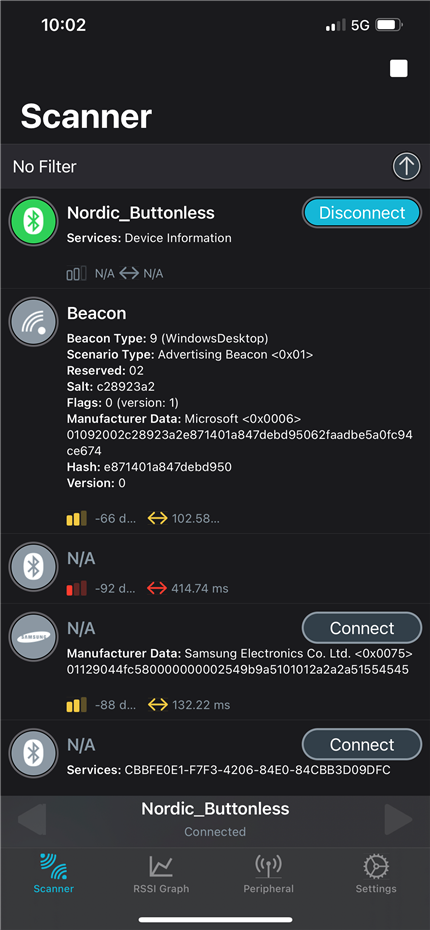
I've programmed "sd_s132_bootloader_buttonless_with_setting_page_dfu_secure_ble_debug_with_bonds" HEX file to the device and am working towards creating the bond with the phone per below.
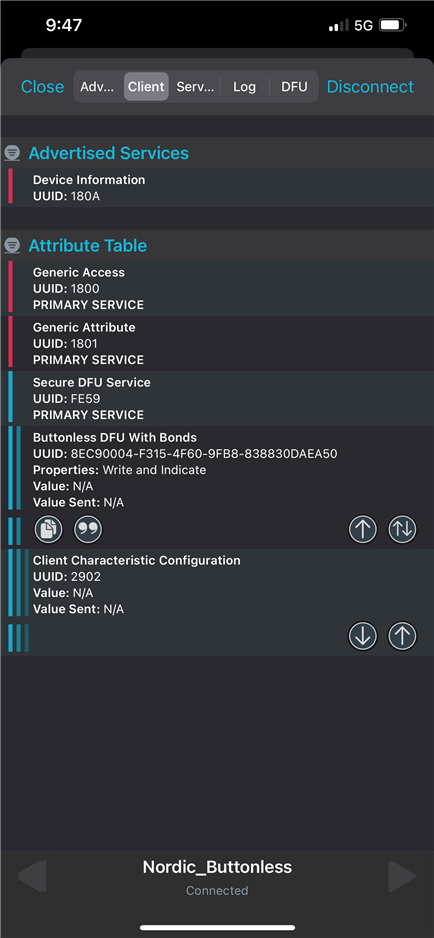
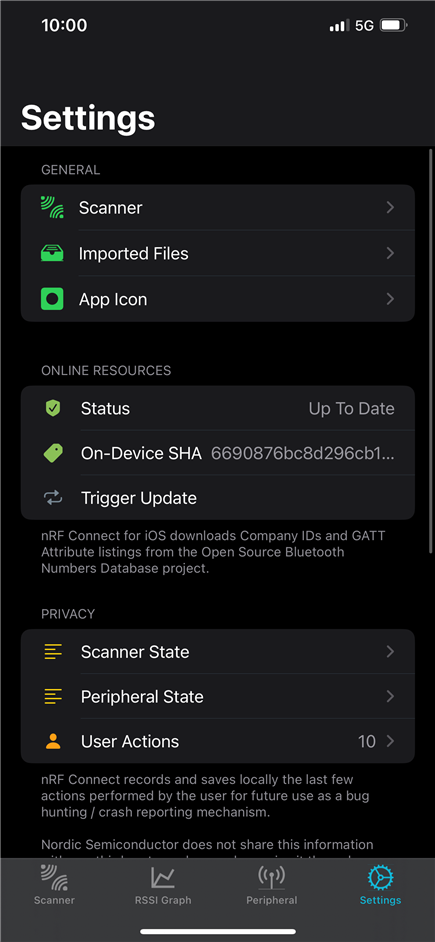
Bond to the device using nRF Connect (it is advertising as 'Nordic_Buttonless'). Click the settings button, select "Security Settings", check "Perform bonding", and click "Apply".
but am having issues finding the "security setting" or "perform bonding" button in this version of the nRF Connect app. Any help with navigating the app is MUCH appreciated, once I learn how to make the connection, I can try and troubleshoot from there.
Please let me know if I'm leaving anything out, I've done a lot of steps up to this point.
Thank you, Gerald


