I'm experimenting with the nrf91 https example to simulate my use case. In general my device will come online hourly and send some data, get a 204 response back from the server, then go to sleep again until the next hour.
For development i've configured the a 2 minute PSM. Every 2 minutes I send establish a connection to my server with a new socket, send the data, then close the socket (both server side and client side).
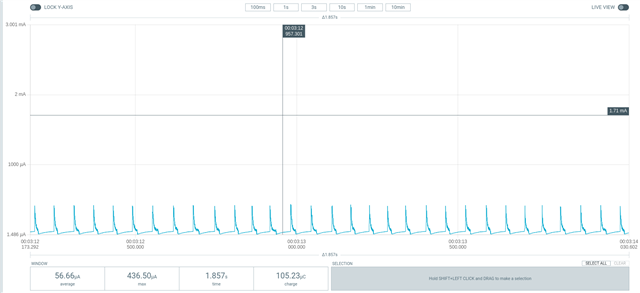
The first time I do this, everything works fine. After sending data and closing the connection the modem goes into psm mode with a very low ~2.9ua current, but when i go ahead and establish the second connection, that never happens. instead after going to sleep i see regular 428 ua spikes.
I know i can reuse the socket, but i'd rather not. My understanding is the modem should be detecting that there's no more data available on the network and should be putting the modem to sleep.
my config is as follows. I'm including a modem trace as well, and some screenshots of my power profile. I'm at a bit of a loss here.
CONFIG_NRF_MODEM_LIB=y CONFIG_NETWORKING=y CONFIG_NET_SOCKETS=y CONFIG_NET_SOCKETS_POSIX_NAMES=y CONFIG_NET_NATIVE=n CONFIG_HEAP_MEM_POOL_SIZE=1024 CONFIG_MAIN_STACK_SIZE=2048 CONFIG_MODEM_KEY_MGMT=y CONFIG_LTE_LINK_CONTROL=y # Request eDRX from the network # https://aeriscom.zendesk.com/hc/en-us/articles/360049848254-Understanding-LTE-M-Power-Management-Modes # PSM requested periodic TAU 1 hours # CONFIG_LTE_PSM_REQ_RPTAU="00100001" # PSM requested periodic TAU 2 minutes CONFIG_LTE_PSM_REQ_RPTAU="10100010" # PSM requested active time 1 seconds (immediate PSM) CONFIG_LTE_PSM_REQ_RAT="00011111" # edrx value ~ 1 hour # CONFIG_LTE_RAI_REQ_VALUE="4" CONFIG_LTE_AUTO_INIT_AND_CONNECT=y CONFIG_NEWLIB_LIBC=y # General options to reduce code size CONFIG_CONSOLE=n CONFIG_GPIO=n CONFIG_LOG=n CONFIG_PRINTK=n CONFIG_SERIAL=n CONFIG_UART_CONSOLE=n # Set explicitly to 'n' to avoid Kconfig warning CONFIG_USE_SEGGER_RTT=n CONFIG_BOOT_BANNER=n CONFIG_NET_SOCKETS_OFFLOAD=y CONFIG_NRF_MODEM_LIB_TRACE=n
trace-2023-03-07T16-34-51.160Z.pcapng
After the first connection:
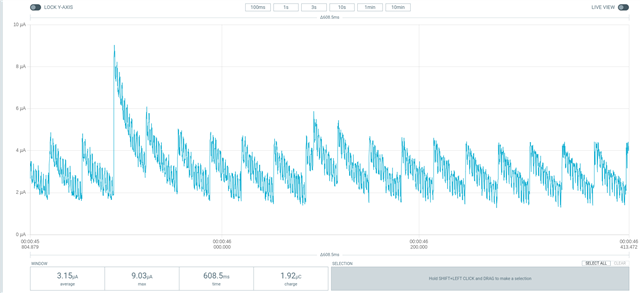
After any subsequent connections: