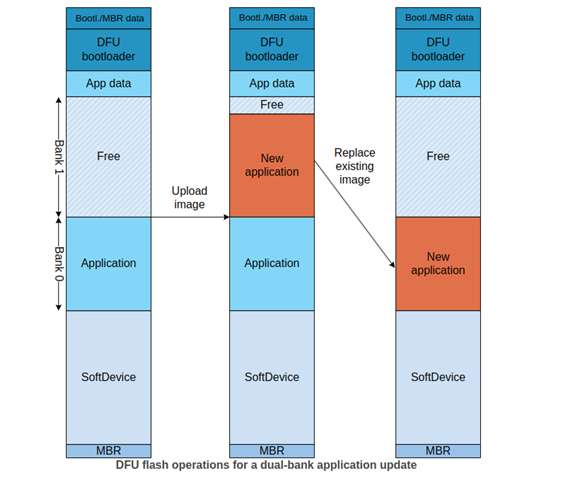
Our company has an existing product (snodar) which uses an nRF52840. When we created the snodar, it used a bootloader based on the `secure_bootloader` project. On top of that, we are using the s140 SD and have an APP which allows DFU over BLE. We have been able to update the snodar over BLE using the nordic DFU tools or our own custom Android/iOS apps.
We also have another product (gateway) which uses an nRF52840 + nRF9160. I've been working on mechanism to update the snodar by transferring the firmware over ESB using the gateway then doing an in-place DFU on the snodar. This works only if I can replace the bootloader on the snodar. To get the in-place DFU to work, I had to make a couple of changes to the bootloader project.
{
FLASH (rx) : ORIGIN = 0xf7000, LENGTH = 0x7000
RAM (rwx) : ORIGIN = 0x20005978, LENGTH = 0x3a688
uicr_bootloader_start_address (r) : ORIGIN = 0x10001014, LENGTH = 0x4
bootloader_settings_page (r) : ORIGIN = 0x000FF000, LENGTH = 0x1000
uicr_mbr_params_page (r) : ORIGIN = 0x10001018, LENGTH = 0x4
mbr_params_page (r) : ORIGIN = 0x000FE000, LENGTH = 0x1000
}
{
FLASH (rx) : ORIGIN = 0x27000, LENGTH = 0xc9000
RAM (rwx) : ORIGIN = 0x20006368, LENGTH = 0x39c98
uicr_bootloader_start_address (r) : ORIGIN = 0x10001014, LENGTH = 0x4
}
SECTIONS
{
. = ALIGN(4);
.uicr_bootloader_start_address :
{
PROVIDE(__start_uicr_bootloader_start_address = .);
KEEP(*(SORT(.uicr_bootloader_start_address*)))
PROVIDE(__stop_uicr_bootloader_start_address = .);
} > uicr_bootloader_start_address
}
00> bin len/crc = 284644, 97038ff8
00> *** Trigger DFU ***
00> ~~ RTC ptimer disabled
00> CRC ok?
00> dat: b100ec1e - b100ec1e -> 1
00> bin: 97038ff8 - 97038ff8 -> 1
00> Starting DFU update: bin_addr = 3f81000, remaining = 284644
00> <info> app: NRF_DFU_EVT_DFU_STARTED
00>
00> <info> nrf_dfu_validation: Signature required. Checking signature.
00>
00> <info> nrf_dfu_validation: Calculating hash (len: 65)
00>
00> <info> nrf_dfu_validation: Verify signature
00>
00> <info> nrf_dfu_validation: Image verified
00>
00> <warning> nrf_dfu_settings: Settings write aborted since it tries writing to forbidden settings.
00>
00> <warning> nrf_dfu_serial: DFU request completed with result: 0xA
00>
00> <info> app: NRF_DFU_EVT_DFU_FAILED
{
FLASH (rx) : ORIGIN = 0x27000, LENGTH = 0xc9000
RAM (rwx) : ORIGIN = 0x20006368, LENGTH = 0x39c98
uicr_bootloader_start_address (r) : ORIGIN = 0x10001014, LENGTH = 0x4
bootloader_settings_page (r) : ORIGIN = 0x000FF000, LENGTH = 0x1000
uicr_mbr_params_page (r) : ORIGIN = 0x10001018, LENGTH = 0x4
mbr_params_page (r) : ORIGIN = 0x000FE000, LENGTH = 0x1000
}
SECTIONS
{
. = ALIGN(4);
.uicr_bootloader_start_address :
{
PROVIDE(__start_uicr_bootloader_start_address = .);
KEEP(*(SORT(.uicr_bootloader_start_address*)))
PROVIDE(__stop_uicr_bootloader_start_address = .);
} > uicr_bootloader_start_address
. = ALIGN(4);
.bootloader_settings_page(NOLOAD) :
{
PROVIDE(__start_bootloader_settings_page = .);
KEEP(*(SORT(.bootloader_settings_page*)))
PROVIDE(__stop_bootloader_settings_page = .);
} > bootloader_settings_page
. = ALIGN(4);
.uicr_mbr_params_page :
{
PROVIDE(__start_uicr_mbr_params_page = .);
KEEP(*(SORT(.uicr_mbr_params_page*)))
PROVIDE(__stop_uicr_mbr_params_page = .);
} > uicr_mbr_params_page
. = ALIGN(4);
.mbr_params_page(NOLOAD) :
{
PROVIDE(__start_mbr_params_page = .);
KEEP(*(SORT(.mbr_params_page*)))
PROVIDE(__stop_mbr_params_page = .);
} > mbr_params_page
}
nrfutil settings generate --family NRF52840 --application "${APP_NAME}.hex" --application-version 0 --bootloader-version 1 --bl-settings-version 2 settings.hex
mergehex -m "${APP_NAME}.hex" *_softdevice.hex "nrf52840_xxaa_s140.hex" -o tmp.hex
mergehex -m tmp.hex settings.hex -o "${PROD_FW}_v${FW_VER}.hex"
rm tmp.hex