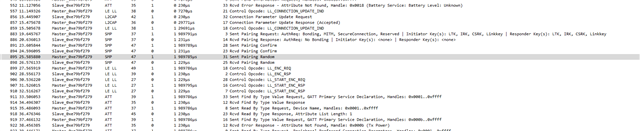
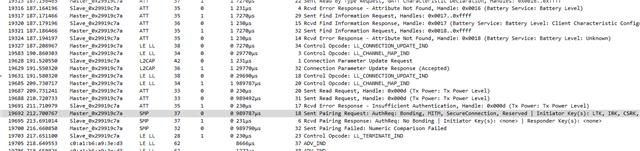
I've noticed on the nRF Connect phone app that there is a bond button. If I'm in just works pairing no bonding mode (settings below), and click the bond button a bond still appears to be done. However, when sniffing the packets I know that the phone acknowledges my security parameters, where I say bonding is not allowed. However it seems like a bond still happens on the phone, but not on the nRF chip. I assume the nRF does not save any keys, which is why when trying to connect again I have to re-pair. I would guess it's the phone's operating system (Android/IOS) that is still trying to make a bond.
sec_param.bond = false; sec_param.mitm = false; sec_param.lesc = 0; sec_param.keypress = 0; sec_param.io_caps = BLE_GAP_IO_CAPS_NONE; sec_param.oob = false; sec_param.min_key_size = 7; sec_param.max_key_size = 16; sec_param.kdist_own.enc = 0; sec_param.kdist_own.id = 0; sec_param.kdist_peer.enc = 0; sec_param.kdist_peer.id = 0;
If what I am saying makes sense, is there any way to stop bonding requests, but still allow pairing? I know that setting the sec_param.bond = false" won't make a bond, but I want if someone tries to bond reject it completely, as opposed to don't allowing the bond but still allow pairing, i.e if it's a bond request reject it completely, if it's a pairing request pass it through.
I know this article shows how to stop bonding, but this also stops pairing as it uses the BLE_GAP_SEC_STATUS_PAIRING_NOT_SUPP parameter, which as expected stops pairing.
https://jimmywongiot.com/2021/06/29/how-to-allow-reject-the-ble-bonding-request-from-central/