Hi,
I have bought an nRF52DK (PCA10040 v3.0.0), which has an nRF5340 chip.
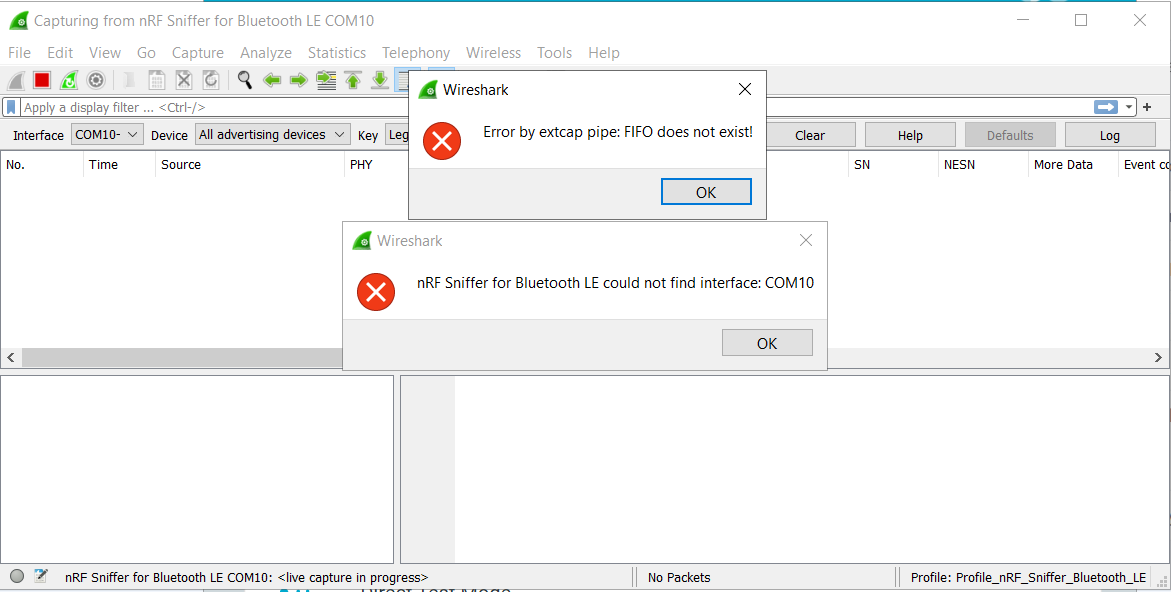
I want to use it as BLE Sniffer to debug my application, but Wireshark is giving me an error "FIFO while trying to access the nRF 52 DK.
.
I followed everything written in the documentation from:
https://www.nordicsemi.com/Products/Development-tools/nrf-sniffer-for-bluetooth-le
I installed the sniffer_nrf52dk_nrf52832_4.1.1.hex into my nRF52 DK.
Wireshark is able to detect the board at COM10.
I'm running Wireshark as an admin too.
My current setup:
Intel(R) Core(TM) i5-6300U CPU @ 2.40GHz 2.50 GHz, 8GB RAM
Windows 10 Pro 64bits
Python: Python 3.9.10
WireShark Version 4.0.5
Result from testing in the Windows cmd "nrf_sniffer_ble.bat --extcap-interfaces"
extcap {version=4.1.1}{display=nRF Sniffer for Bluetooth LE}{help=www.nordicsemi.com/.../nRF-Sniffer-for-Bluetooth-LE}
control {number=0}{type=selector}{display=Device}{tooltip=Device list}
control {number=1}{type=selector}{display=Key}{tooltip=}
control {number=2}{type=string}{display=Value}{tooltip=6 digit passkey or 16 or 32 bytes encryption key in hexadecimal starting with '0x', big endian format.If the entered key is shorter than 16 or 32 bytes, it will be zero-padded in front'}{validation=\b^(([0-9]{6})|(0x[0-9a-fA-F]{1,64})|([0-9A-Fa-f]{2}[:-]){5}([0-9A-Fa-f]{2}) (public|random))$\b}
control {number=3}{type=string}{display=Adv Hop}{default=37,38,39}{tooltip=Advertising channel hop sequence. Change the order in which the sniffer switches advertising channels. Valid channels are 37, 38 and 39 separated by comma.}{validation=^\s*((37|38|39)\s*,\s*){0,2}(37|38|39){1}\s*$}{required=true}
control {number=7}{type=button}{display=Clear}{tooltop=Clear or remove device from Device list}
control {number=4}{type=button}{role=help}{display=Help}{tooltip=Access user guide (launches browser)}
control {number=5}{type=button}{role=restore}{display=Defaults}{tooltip=Resets the user interface and clears the log file}
control {number=6}{type=button}{role=logger}{display=Log}{tooltip=Log per interface}
value {control=0}{value= }{display=All advertising devices}{default=true}
value {control=0}{value=[00,00,00,00,00,00,0]}{display=Follow IRK}
value {control=1}{value=0}{display=Legacy Passkey}{default=true}
value {control=1}{value=1}{display=Legacy OOB data}
value {control=1}{value=2}{display=Legacy LTK}
value {control=1}{value=3}{display=SC LTK}
value {control=1}{value=4}{display=SC Private Key}
value {control=1}{value=5}{display=IRK}
value {control=1}{value=6}{display=Add LE address}
value {control=1}{value=7}{display=Follow LE address}
Also adding part of the log file from "AppData\Roaming\Nordic Semiconductor\Sniffer\logs\log.txt"
30-Apr-2023 18:57:23 (+0800) INFO: --------------------------------------------------------
30-Apr-2023 18:57:23 (+0800) INFO: Software version: 4.1.1
30-Apr-2023 18:57:23 (+0800) INFO: Started PID 4212
30-Apr-2023 18:57:23 (+0800) INFO: Namespace(capture=True, extcap_interfaces=False, extcap_interface='COM10-4.0', extcap_dlts=False, extcap_config=False, extcap_capture_filter=None, fifo='\\\\.\\pipe\\wireshark_extcap_COM10-4.0_20230430185718', extcap_control_in='\\\\.\\pipe\\wireshark_control_ws_to_ext_COM10-4.0_20230430185718', extcap_control_out='\\\\.\\pipe\\wireshark_control_ext_to_ws_COM10-4.0_20230430185718', extcap_version=None, device='', baudrate=None, only_advertising=False, only_legacy_advertising=False, scan_follow_rsp=True, scan_follow_aux=True, coded=False)
30-Apr-2023 18:57:23 (+0800) INFO: sniffer capture
30-Apr-2023 18:57:23 (+0800) INFO: Log started at Sun Apr 30 18:57:23 2023
30-Apr-2023 18:57:23 (+0800) INFO: Extcap version 4.0
30-Apr-2023 18:57:23 (+0800) INFO: Opening serial port COM10
30-Apr-2023 18:57:24 (+0800) INFO: closing UART
30-Apr-2023 18:57:24 (+0800) INFO: Opening serial port COM10
30-Apr-2023 18:57:24 (+0800) INFO: closing UART
30-Apr-2023 18:57:24 (+0800) INFO: Tearing down
30-Apr-2023 18:57:24 (+0800) INFO: Traceback (most recent call last):
File "C:\Users\joaoc\AppData\Roaming\Wireshark\extcap\nrf_sniffer_ble.py", line 613, in sniffer_capture
baudrate = get_default_baudrate(interface, fifo)
File "C:\Users\joaoc\AppData\Roaming\Wireshark\extcap\nrf_sniffer_ble.py", line 557, in get_default_baudrate
error_interface_not_found(interface, fifo)
File "C:\Users\joaoc\AppData\Roaming\Wireshark\extcap\nrf_sniffer_ble.py", line 544, in error_interface_not_found
sys.exit(ERROR_INTERFACE)
SystemExit: 2
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "C:\Users\joaoc\AppData\Roaming\Wireshark\extcap\nrf_sniffer_ble.py", line 843, in <module>
sniffer_capture(interface, args.baudrate, args.fifo, args.extcap_control_in, args.extcap_control_out)
File "C:\Users\joaoc\AppData\Roaming\Wireshark\extcap\nrf_sniffer_ble.py", line 674, in sniffer_capture
sniffer.doExit()
UnboundLocalError: local variable 'sniffer' referenced before assignment
30-Apr-2023 18:57:24 (+0800) INFO: internal error: UnboundLocalError("local variable 'sniffer' referenced before assignment")
30-Apr-2023 18:57:24 (+0800) INFO: Exiting PID 4212
30-Apr-2023 19:03:43 (+0800) INFO: --------------------------------------------------------