Hi,
At first I've succesfully managed to get the central_uart and peripheral_uart example running on 2 custom boards with nRF5340. Both are connecting and pairing fine, I see that they are switching to security level 2 as expected.
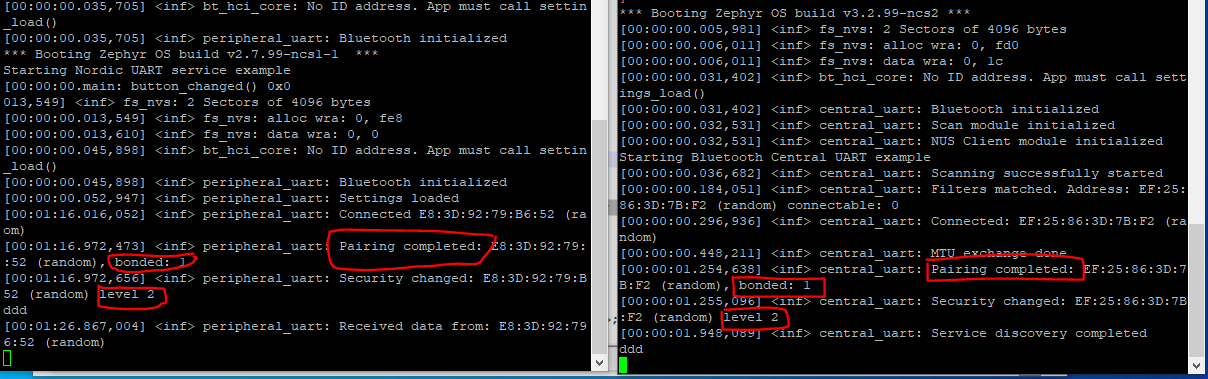
But after a while, after doing nothing special I get security failed error's. I have tried these examples both in nrf 1.9.1 and nrf 2.3.0. Same result: at first it worked but after a while I got the security error's.
A lot of experiments, such as going back to the original examples without changing any code (other then some minimum changes (3 lines) in the board files to get it running) did not fix the problem. Trying to unbond by using the bt_unpair() function did not help.
The only situation I can reproduce that works is to put use the central_uart example from nrf2.3.0 in combination with the peripheral_uart example from nrf 1.9.1. as can be seen in the top picture.
Can somebody please give me some pointers on what is going on?
Any help greatly appreciated,
Arno