Hi,
I have a few questions on key/certificate storage on the nRF9160, specifically relating to getting ready to provision them for production
In the image below, its looks like the application core and LTE modem core have separate embedded flash storage.
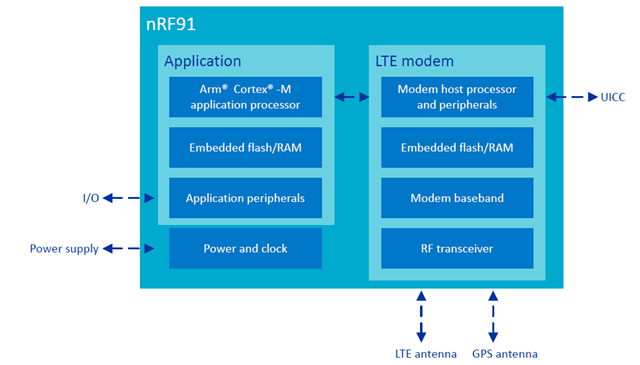
- I am a bit confused by this as the modem firmware, which I assumed is stored on its own embedded flash, can be programmed through nrfjprog / nRF Connect programmer via Jlink. Are the memories linked? How is this happening?
- The extract from the 9160PS below says that the KMU is stored in the UICR, however ensuring the CPU has no access to stored cryptographic keys. When I erase the UICR on nrfjprog, the keys still remain. Is this a different memory sector or modem specific memory UICR? I know the keys are meant to be erased via the AT commands on the modem COM, I'm just trying to understand more about the memory layout

- I have been updating certificates using both the nRFConnect LTE link monitor, which operates on the modem COM port, and a custom program sending out AT commands on the modem COM port. Are there any other methods i.e. via Jlink?
- What keys/certificates are preprogrammed in the nRF9160 SiP (not DK) from the factory?
Thanks!
Kind regards,
Chris


