Hi there,
I'm running the peripheral_hids_keyboard sample of the nRF Connect SDK 2.5.1 on my nRF52840-DK. After pushing button 4, advertising starts as expected, but I can only connect with some of my phones/tablets.
I can connect with:
- OnePlus 9 Pro phone running Android 13
- Huawei P20 Pro running Android 10
I can't connect with:
- MacBook Air running macOS Ventura 13.6.3 - After pressing the Connect button, a progress indicator shortly appears and then disappears.
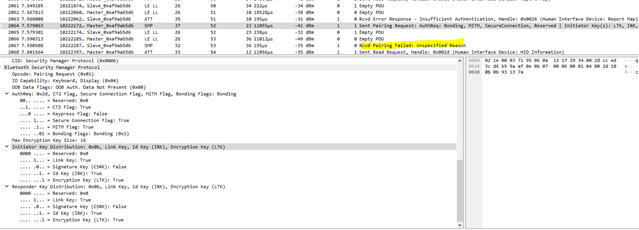
- Huawei MediaPad M5 lite 10 tablet running Android 8.0.0 - Upon trying to pair, I get the "Pairing failed. Incorrect pairing key or the device you want to pair with is configured incorrectly" message.
- NPad-Pro tablet running Android 12 - "Pairing..." momentarily appears, then disappears.
The sample doesn't show up in the Bluetooth devices list:
- ThinkPad T520 running Windows 20 Pro 22H2
Can you reproduce such discrepancies across various hosts, and can you make them connect?