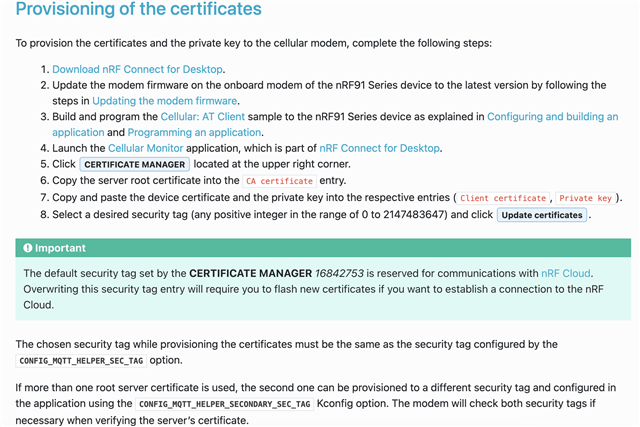
I am an undergrad student who is working on an IoT project utilizing the nRF7002DK board. I am very new to the Nordic NRF SDK and I'm attempting to use the azure_iot_hub sample code to connect my board to my Azure IoT Hub using WiFi. However, I'm facing challenges with the integration of the necessary security certificates into the code. Specifically, I'm unsure about the steps required to add the CA certificate, client certificate, and private key to the project configuration.
I am using v2.5.0 SDK and Toolchains.
I attempted to upload the certificates onto the board utilizing the Nordic Cellular Monitor, only to discover that this approach is exclusively compatible with the nRF91 series, making it useless for the nRF7002DK.
After some research, I added these Kconfig options to my prj.conf:
#
# Copyright (c) 2020 Nordic Semiconductor ASA
#
# SPDX-License-Identifier: LicenseRef-Nordic-5-Clause
#
# General config
CONFIG_REBOOT=y
# Logging
CONFIG_LOG=y
CONFIG_LOG_MODE_DEFERRED=y
# Network
CONFIG_NETWORKING=y
CONFIG_NET_NATIVE=y
CONFIG_NET_IPV4=y
CONFIG_NET_CONNECTION_MANAGER=y
# Azure IoT Hub library
CONFIG_AZURE_IOT_HUB=y
CONFIG_AZURE_IOT_HUB_DEVICE_ID="deviceid"
# Host name must be configured if DPS is not used
CONFIG_AZURE_IOT_HUB_HOSTNAME="hostname"
# Change the security tag to the tag where Azure IoT Hub certificates
# are provisioned
CONFIG_MQTT_HELPER_SEC_TAG=10
CONFIG_MQTT_HELPER_SECONDARY_SEC_TAG=-1
CONFIG_MQTT_HELPER_STACK_SIZE=8192
CONFIG_MQTT_HELPER_PROVISION_CERTIFICATES=y
CONFIG_MQTT_HELPER_CERTIFICATES_FILE="mqtt-certs.h"
# Uncomment to get more verbose logging when debugging
CONFIG_AZURE_IOT_HUB_LOG_LEVEL_DBG=y
# MQTT - Maximum MQTT keepalive timeout specified by Azure IoT Hub
CONFIG_MQTT_KEEPALIVE=1767
# cJSON
CONFIG_CJSON_LIB=y
# Settings, needed for Azure Device Provisioning Service
CONFIG_FLASH=y
CONFIG_FLASH_MAP=y
CONFIG_FCB=y
CONFIG_SETTINGS=y
CONFIG_SETTINGS_FCB=y
CONFIG_MPU_ALLOW_FLASH_WRITE=y
nrf7002dk_nrf5340_cpuapp.conf
#
# Copyright (c) 2023 Nordic Semiconductor ASA
#
# SPDX-License-Identifier: LicenseRef-Nordic-5-Clause
#
# General
CONFIG_POSIX_CLOCK=y
CONFIG_HW_STACK_PROTECTION=y
CONFIG_HW_ID_LIBRARY=y
CONFIG_HW_ID_LIBRARY_SOURCE_NET_MAC=y
CONFIG_DK_LIBRARY=y
# Heap and stacks
CONFIG_MAIN_STACK_SIZE=4096
CONFIG_SYSTEM_WORKQUEUE_STACK_SIZE=4096
CONFIG_HEAP_MEM_POOL_SIZE=153600
CONFIG_NET_RX_STACK_SIZE=2048
# Set newlib C to prevent build error complaining that string.h is not supported
CONFIG_NEWLIB_LIBC_FLOAT_PRINTF=y
# Wi-Fi
CONFIG_WIFI=y
CONFIG_WIFI_NRF700X=y
CONFIG_WIFI_LOG_LEVEL_ERR=y
CONFIG_WIFI_MGMT_EXT=y
CONFIG_WIFI_CREDENTIALS=y
CONFIG_WIFI_CREDENTIALS_BACKEND_SETTINGS=y
CONFIG_WIFI_CREDENTIALS_STATIC=y
CONFIG_FLASH=y
CONFIG_FLASH_PAGE_LAYOUT=y
CONFIG_FLASH_MAP=y
CONFIG_NVS=y
CONFIG_SETTINGS=y
CONFIG_SETTINGS_NVS=y
# WPA
CONFIG_WPA_SUPP=y
CONFIG_WPA_SUPP_LOG_LEVEL_ERR=y
# Zephyr NET Connection Manager connectivity layer
CONFIG_L2_WIFI_CONNECTIVITY=y
CONFIG_L2_WIFI_CONNECTIVITY_AUTO_DOWN=n
# DNS
CONFIG_DNS_RESOLVER=y
# Wi-Fi
CONFIG_WIFI_CREDENTIALS_STATIC_SSID="ssid"
CONFIG_WIFI_CREDENTIALS_STATIC_PASSWORD="password"
# NET sockets
CONFIG_NETWORKING=y
CONFIG_NET_NATIVE=y
CONFIG_NET_SOCKETS=y
CONFIG_NET_L2_ETHERNET=y
CONFIG_NET_IPV4=y
CONFIG_NET_TCP=y
CONFIG_NET_TCP_WORKQ_STACK_SIZE=2048
CONFIG_NET_UDP=y
CONFIG_NET_SOCKETS_OFFLOAD=n
CONFIG_NET_NATIVE=y
CONFIG_NET_DHCPV4=y
CONFIG_NET_CONTEXT_SNDTIMEO=y
CONFIG_NET_CONTEXT_RCVTIMEO=y
CONFIG_NET_MGMT_EVENT_STACK_SIZE=4096
# TLS networking
CONFIG_POSIX_MAX_FDS=14
CONFIG_NET_SOCKETS_SOCKOPT_TLS=y
CONFIG_NET_SOCKETS_ENABLE_DTLS=n
CONFIG_NET_SOCKETS_TLS_MAX_CONTEXTS=2
# nRF Security
CONFIG_NRF_SECURITY=y
CONFIG_PSA_CRYPTO_DRIVER_OBERON=n
CONFIG_CC3XX_BACKEND=y
# mbedTLS
CONFIG_MBEDTLS=y
CONFIG_MBEDTLS_ENABLE_HEAP=y
CONFIG_MBEDTLS_HEAP_SIZE=120000
CONFIG_MBEDTLS_RSA_C=y
# FOTA
CONFIG_AZURE_FOTA=y
CONFIG_AZURE_FOTA_APP_VERSION_AUTO=n
CONFIG_AZURE_FOTA_TLS=y
# Change the security tag to the tag where the certificates are provisioned
# for the server where the FOTA image is hosted
CONFIG_AZURE_FOTA_SEC_TAG=11
CONFIG_BOOTLOADER_MCUBOOT=y
CONFIG_FOTA_DOWNLOAD=y
CONFIG_DFU_TARGET=y
CONFIG_MCUBOOT_IMG_MANAGER=y
CONFIG_IMG_MANAGER=y
CONFIG_STREAM_FLASH=y
CONFIG_FLASH_MAP=y
CONFIG_FLASH=y
CONFIG_IMG_ERASE_PROGRESSIVELY=y
CONFIG_DOWNLOAD_CLIENT=y
CONFIG_DOWNLOAD_CLIENT_STACK_SIZE=4096
# Enable external flash to host MCUBoot secondary partition
CONFIG_SPI=y
CONFIG_SPI_NOR=y
CONFIG_SPI_NOR_SFDP_DEVICETREE=y
CONFIG_PM_OVERRIDE_EXTERNAL_DRIVER_CHECK=y
mqtt-certs.h: /*
* Copyright (c) 2023 Nordic Semiconductor ASA
*
* SPDX-License-Identifier: LicenseRef-Nordic-5-Clause
*/
/*
* "-----BEGIN CA CERTIFICATE-----\n"
* "-----CERTIFICATE-----\n"
* "-----END CA CERTIFICATE-----\n"
*/
static const unsigned char ca_certificate[] = {
#if __has_include("ca-cert.pem")
#include "ca-cert.pem"
#else
"-----BEGIN CERTIFICATE-----\n"
"-----CERTIFICATE-----\n"
"-----END CERTIFICATE-----\n"
#endif
};
/*
* "-----BEGIN PRIVATE KEY-----\n"
* "-----KEY-----\n"
* "-----END PRIVATE KEY-----\n"
*/
static const unsigned char private_key[] = {
#if __has_include("private-key.pem")
#include "private-key.pem"
#else
"-----BEGIN RSA PRIVATE KEY-----\n"
"-----CERTIFICATE-----\n"
"-----END RSA PRIVATE KEY-----\n"
#endif
};
/*
* "-----BEGIN CLIENT CERTIFICATE-----\n"
* "-----CERTIFICATE-----\n"
* "-----END CLIENT CERTIFICATE-----\n"
*/
static const unsigned char device_certificate[] = {
#if __has_include("client-cert.pem")
#include "client-cert.pem"
#else
"-----BEGIN CERTIFICATE-----\n"
"-----CERTIFICATE-----\n"
"-----END CERTIFICATE-----\n"
#endif
};
#if CONFIG_MQTT_HELPER_SECONDARY_SEC_TAG != -1
/*
* "-----BEGIN CA CERTIFICATE-----\n"
* "-----CERTIFICATE-----\n"
* "-----END CA CERTIFICATE-----\n"
*/
static const unsigned char ca_certificate_2[] = {
#if __has_include("ca-cert-2.pem")
#include "ca-cert-2.pem"
#else
""
#endif
};
/*
* "-----BEGIN PRIVATE KEY-----\n"
* "-----KEY-----\n"
* "-----END PRIVATE KEY-----\n"
*/
static const unsigned char private_key_2[] = {
#if __has_include("private-key-2.pem")
#include "private-key-2.pem"
#else
""
#endif
};
/*
* "-----BEGIN CLIENT CERTIFICATE-----\n"
* "-----CERTIFICATE-----\n"
* "-----END CLIENT CERTIFICATE-----\n"
*/
static const unsigned char device_certificate_2[] = {
#if __has_include("client-cert-2.pem")
#include "client-cert-2.pem"
#else
""
#endif
};
#endif /* CONFIG_MQTT_HELPER_SECONDARY_SEC_TAG != -1 */
nrf7002dk_nrf5340_cpuapp.overlay is the same as the sample.
main.c is the same as the sample.
This is how I build the application:

When I build and flash the application, this is the output I receive from my board:
*** Booting nRF Connect SDK v2.5.0 *** OK OK OK OK OK OK [00:00:00.014,801] <inf> spi_nor: mx25r6435f@0: 8 MiBy flash [00:00:00.224,029] <inf> fs_nvs: 2 Sectors of 4096 bytes [00:00:00.224,029] <inf> fs_nvs: alloc wra: 0, fe8 [00:00:00.224,029] <inf> fs_nvs: data wra: 0, 0 *** Booting nRF Connect SDK v2.5.0 *** [00:00:00.224,456] <inf> azure_iot_hub_sample: Azure IoT Hub sample started [00:00:00.224,456] <inf> azure_iot_hub_sample: Bringing network interface up and connecting to the network [00:00:01.595,947] <inf> azure_iot_hub_sample: Device ID: deviceid [00:00:01.595,977] <inf> azure_iot_hub_sample: Host name: hostname [00:00:06.848,693] <inf> azure_iot_hub_sample: Network connectivity established and IP address assigned [00:00:06.849,456] <inf> azure_iot_hub_sample: Connected to network [00:00:06.850,250] <inf> azure_fota: Current firmware version: 0.0.0-dev [00:00:06.850,250] <dbg> azure_iot_hub: azure_iot_hub_init: Azure FOTA initialized [00:00:06.850,280] <dbg> azure_iot_hub: iot_hub_state_set: State transition: STATE_UNINIT --> STATE_DISCONNECTED [00:00:06.850,311] <inf> azure_iot_hub_sample: Azure IoT Hub library initialized [00:00:06.850,341] <dbg> azure_iot_hub: iot_hub_state_set: State transition: STATE_DISCONNECTED --> STATE_CONNECTING [00:00:06.850,372] <inf> azure_iot_hub_sample: AZURE_IOT_HUB_EVT_CONNECTING [00:00:06.850,433] <dbg> azure_iot_hub: azure_iot_hub_connect: User name: hostname/deviceid/?api-version=2020-09-30&DeviceClientType=azsdk-c%2F1.4.0-beta.2 [00:00:06.850,433] <dbg> azure_iot_hub: azure_iot_hub_connect: User name buffer size is 160, actual user name size is: 106 [00:00:07.508,666] <err> mqtt_helper: mqtt_connect, error: -2 [00:00:07.508,697] <err> azure_iot_hub: mqtt_helper_connect failed, error: -2 [00:00:07.508,758] <dbg> azure_iot_hub: iot_hub_state_set: State transition: STATE_CONNECTING --> STATE_DISCONNECTED [00:00:07.508,880] <err> azure_iot_hub_sample: azure_iot_hub_connect failed: -2
In terms of my CA certificate, I created it using SSL and had it signed. It was also correctly verified on my Azure IoT Hub:

![]()
If anyone could provide guidance on how to correctly fix this issue or point me towards relevant documentation or examples? Your help would be greatly appreciated! Thank you so much.