Hi all,
Recently I am trying to start a secure MQTT connect between Rabbit MQ broker and nRF-9160 or nRF-9151.
nRF9160 is running Serial LTE Modem(SLM) application with v2.4.0 SDK , and nRF-9151 is also running SLM but under v2.7.0 SDK.
Broker was set to single way MQTTS with credentials applied from "let's encrypt" (or called simple MQTTS as I heard, which only clients would check server, server doesn't check client).
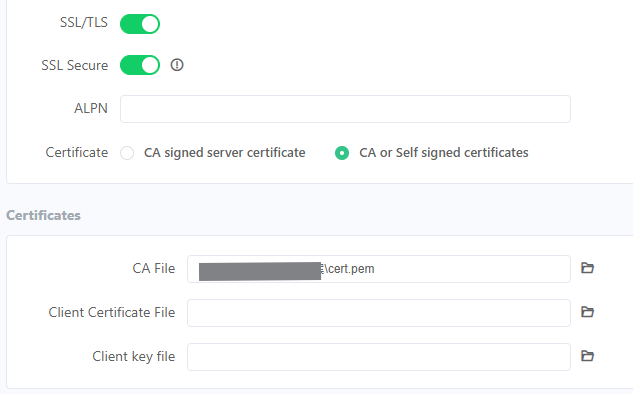
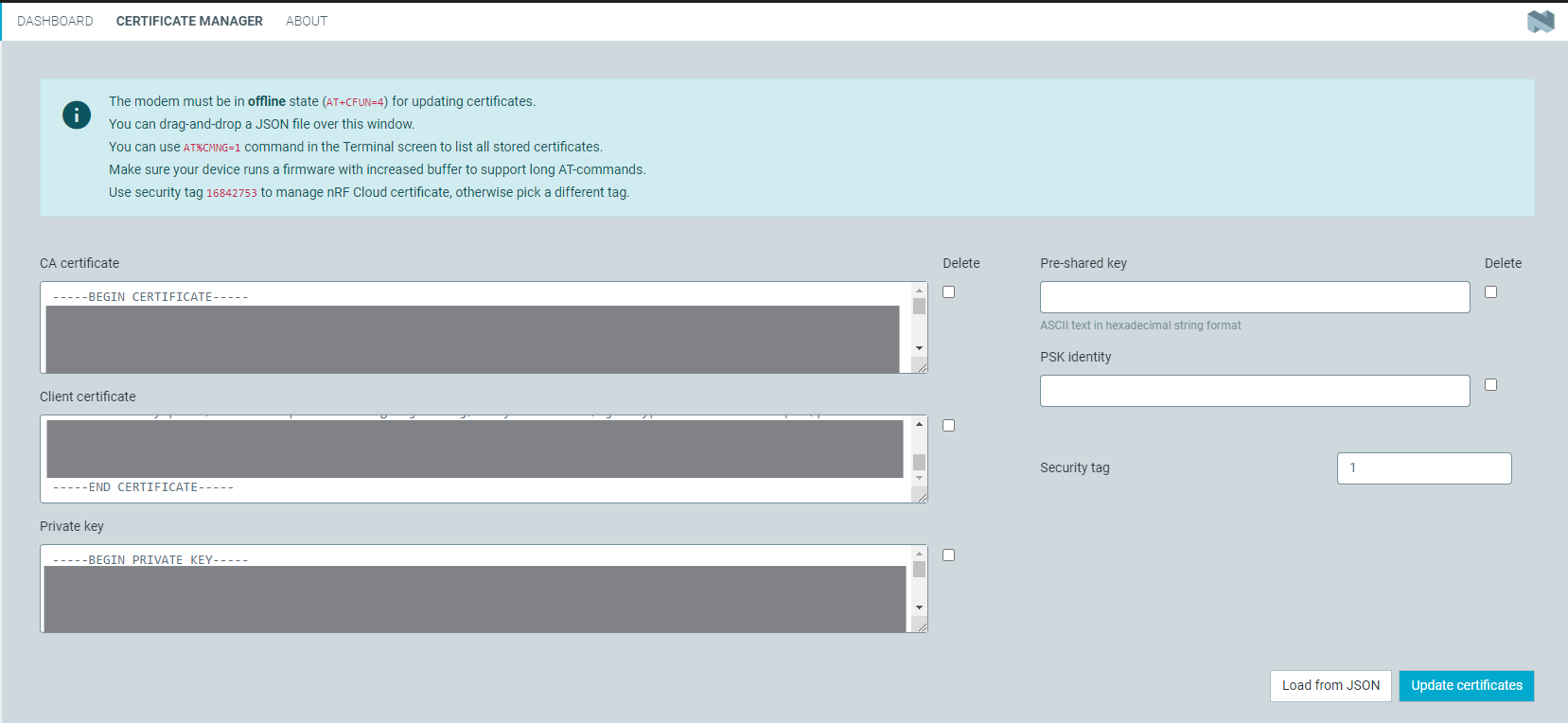
I'm now using PC tool "Cellular Monitor" to import certificate files, and according to the GUI, there could be CA certificate(CA) / Client Certificate(CC) / Private Key(PK).
My questions are:
- According to ChatGPT (might not be correct...):
"when running simple MQTTS,
server needs CA certificate / Server Certificate / Server Private Key,
and clients need Client CA Certificate / Client Private Key, Client Certificate usually is not a must."
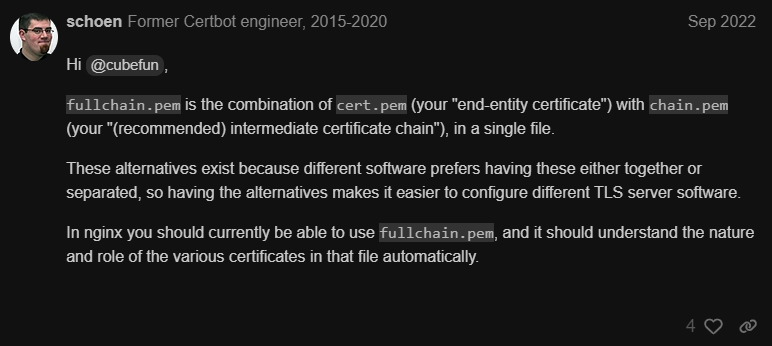
So... does server and clients both use the same CA certificate file? Does server and client need to have different private key file? - I've got 3 files named "cert.pem" "chain.pem" "privkey.pem" provided by server side colleague (I assume these are CA file, CC file and PK file).
However when I import them into SLM with cellular monitor tool, no matter if I feed CA only / CA + PK / CA + CC + PK, AT#XMQTTCON always returns "ERROR"(Any method to found reason of error?).
As I'm surfing trying to find some solution, I noticed that some company requires user to turn .pem files into one-line format before feeding them. So does \r and \n needed to remove before feeding my certificate file into SLM?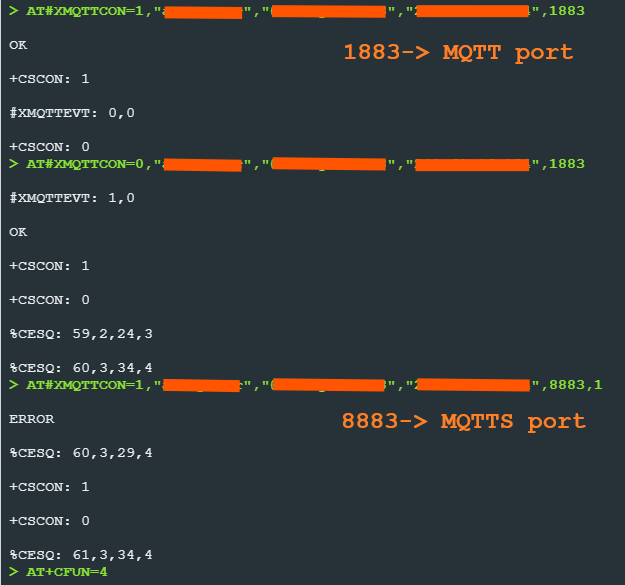
(Connection to MQTT port success, but connection to MQTTS port with <sec_tag> returns ERROR - I've noticed there are a command AT%KEYGEN. But I'm not sure if I need to use this and how do I use this.
As mentioned in question 1, do I have to generate a private key per client by it self or can it just use the same PK file as server?
If it is a must to generate a private key by each client themself, is this the correct command I should use?
The first purpose stated in the page "Client private key and certificate signing request (CSR) (<key_type> 2, <response_content> 0)" seems kind of like what I need, as it says it could be used for TLS credential. But 1st how does it know which CA should it try to apply client certificate + private key (could CA certificate file help?), 2nd we are only doing simple MQTTS so we might not need the generated client certificate, would "extra certificate file" be a concern or we may just ignore it?