nRF Connect VS Code Extension (v2.7.0); Windows; nRF9160DK; https_client example application
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Hello,
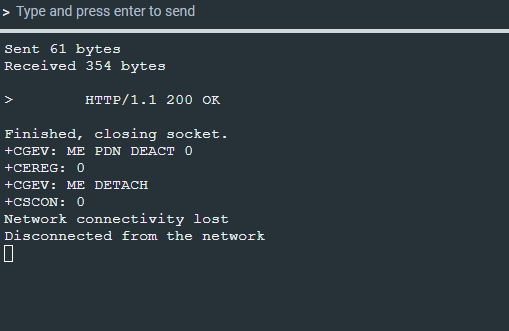
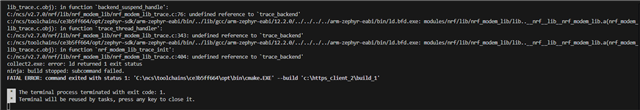
I am currently working with the Nordic nRF9160DK and am using the https_client example from the examples in the nRF Connect via VS Code, and as far as I know it is the latest release (v2.7.0). I have already successfully established a connection with example.com and was able to send/receive data. However, I am having some issues when attempting to change the certificate. I am attempting to connect to dweet.io, and when running the demo, I receive an output which says "Certificate mismatch" and "err: 111" (see image below):
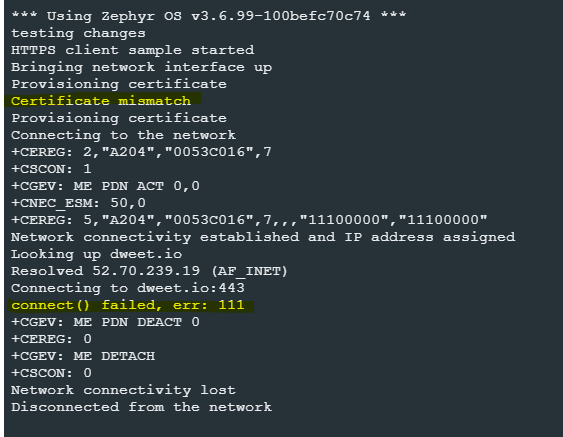
I made the following changes to the source code based on what seemed like it had needed changing and based on previous DevZone posts I have seen with similar issues. I linked the main issue that I followed here: changing certificate in https_client sample
I also referenced the following documentation: https://docs.nordicsemi.com/bundle/ncs-latest/page/nrf/libraries/modem/modem_key_mgmt.html#cert-dwload
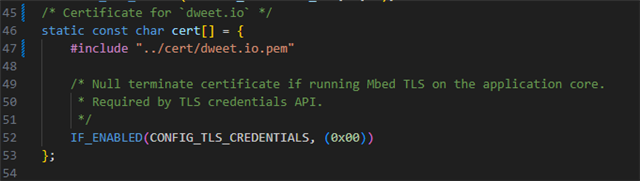
Added the .pem file (filename dweet.io.pem) in the /cert directory, as well as added "...\n":

Updated the certificate definition in main.c:
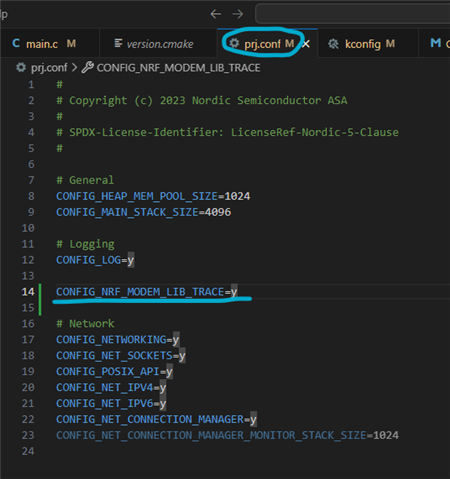
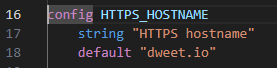
Changed HTTPS_HOSTNAME in kconfig:
Any help in resolving this issue would be greatly appreciated.