Hello,
I am using the nRF Connect SDK v2.9.0. While working on the nRF52840 board, I used the library zephyr/crypto/crypto.h to perform AES/ECB encryption.
Part of the code I wrote is
Hello,
I am using the nRF Connect SDK v2.9.0. While working on the nRF52840 board, I used the library zephyr/crypto/crypto.h to perform AES/ECB encryption.
Part of the code I wrote is
Hi,
Could you try this unofficial patch 0001-drivers-add-support-for-nRF54L-ECB.patch? My colleague makes some changes to support ECB on nRF54L.
Hi,
Could you try this unofficial patch 0001-drivers-add-support-for-nRF54L-ECB.patch? My colleague makes some changes to support ECB on nRF54L.
When I applied this patch file, I got these errors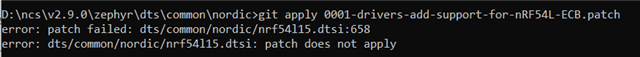
You can refer to the patch and modify it manually.
---
drivers/crypto/Kconfig.nrf_ecb | 11 ++++++-
drivers/crypto/crypto_nrf_ecb.c | 56 ++++++++++++++++++++++++++++++++-
dts/common/nordic/nrf54l15.dtsi | 7 +++++
3 files changed, 72 insertions(+), 2 deletions(-)
diff --git a/drivers/crypto/Kconfig.nrf_ecb b/drivers/crypto/Kconfig.nrf_ecb
index 624baedab09..9945ed62de6 100644
--- a/drivers/crypto/Kconfig.nrf_ecb
+++ b/drivers/crypto/Kconfig.nrf_ecb
@@ -10,6 +10,15 @@ config CRYPTO_NRF_ECB
# Bluetooth controller uses the ECB peripheral directly
# (see subsys/bluetooth/controller/ll_sw/nordic/hal/nrf5/ecb.c),
# hence this driver cannot be enabled together with it.
- depends on !BT_CTLR
+ # Temperary remove dependcy for Gazell and BLE coexistence demo
help
Enable nRF HAL-based AES ECB encryption driver
+
+config CRYPTO_NRF_ECB_MULTIUSER
+ bool
+ depends on CRYPTO_NRF_ECB
+ default y if BT_CTLR
+ help
+ Reassign ECB pointers right before encryption to ensure proper values.
+ This must be done if the ECB peripheral may be used bypassing this
+ driver's API (e.g. Bluetooth Controller bypasses the Zephyr driver).
diff --git a/drivers/crypto/crypto_nrf_ecb.c b/drivers/crypto/crypto_nrf_ecb.c
index 9fa354738ae..d7331e2f42f 100644
--- a/drivers/crypto/crypto_nrf_ecb.c
+++ b/drivers/crypto/crypto_nrf_ecb.c
@@ -8,6 +8,7 @@
#include <zephyr/crypto/crypto.h>
#include <zephyr/logging/log.h>
#include <hal/nrf_ecb.h>
+#include <zephyr/sys/byteorder.h>
#define DT_DRV_COMPAT nordic_nrf_ecb
@@ -17,6 +18,10 @@
LOG_MODULE_REGISTER(crypto_nrf_ecb, CONFIG_CRYPTO_LOG_LEVEL);
struct ecb_data {
+#if defined(CONFIG_SOC_SERIES_NRF54LX)
+ nrf_vdma_job_t in_job;
+ nrf_vdma_job_t out_job;
+#endif /* CONFIG_SOC_SERIES_NRF54LX */
uint8_t key[ECB_AES_KEY_SIZE];
uint8_t cleartext[ECB_AES_BLOCK_SIZE];
uint8_t ciphertext[ECB_AES_BLOCK_SIZE];
@@ -46,6 +51,39 @@ static int do_ecb_encrypt(struct cipher_ctx *ctx, struct cipher_pkt *pkt)
memcpy(drv_state.data.cleartext, pkt->in_buf,
ECB_AES_BLOCK_SIZE);
}
+#if defined(CONFIG_SOC_SERIES_NRF54LX)
+ uint32_t *key_reverse = (uint32_t *)drv_state.data.key;
+
+ /* AES key order should be reversed on nRF54L */
+ nrf_ecb_key_set(NRF_ECB00, (uint32_t[]){
+ __builtin_bswap32(key_reverse[3]),
+ __builtin_bswap32(key_reverse[2]),
+ __builtin_bswap32(key_reverse[1]),
+ __builtin_bswap32(key_reverse[0]),
+ });
+
+ if (IS_ENABLED(CONFIG_CRYPTO_NRF_ECB_MULTIUSER)) {
+ nrf_ecb_in_ptr_set(NRF_ECB00, &drv_state.data.in_job);
+ nrf_ecb_out_ptr_set(NRF_ECB00, &drv_state.data.out_job);
+ }
+
+ drv_state.data.in_job.size = pkt->in_len;
+ drv_state.data.out_job.size = pkt->in_len;
+ nrf_ecb_event_clear(NRF_ECB00, NRF_ECB_EVENT_END);
+ nrf_ecb_event_clear(NRF_ECB00, NRF_ECB_EVENT_ERROR);
+ nrf_ecb_task_trigger(NRF_ECB00, NRF_ECB_TASK_START);
+ while (!(nrf_ecb_event_check(NRF_ECB00, NRF_ECB_EVENT_END) ||
+ nrf_ecb_event_check(NRF_ECB00, NRF_ECB_EVENT_ERROR))) {
+ }
+ if (nrf_ecb_event_check(NRF_ECB00, NRF_ECB_EVENT_ERROR)) {
+ LOG_ERR("ECB operation error");
+ return -EIO;
+ }
+
+#else
+ if (IS_ENABLED(CONFIG_CRYPTO_NRF_ECB_MULTIUSER)) {
+ nrf_ecb_data_pointer_set(NRF_ECB, &drv_state.data);
+ }
nrf_ecb_event_clear(NRF_ECB, NRF_ECB_EVENT_ENDECB);
nrf_ecb_event_clear(NRF_ECB, NRF_ECB_EVENT_ERRORECB);
@@ -57,19 +95,35 @@ static int do_ecb_encrypt(struct cipher_ctx *ctx, struct cipher_pkt *pkt)
LOG_ERR("ECB operation error");
return -EIO;
}
+#endif /* CONFIG_SOC_SERIES_NRF54LX */
if (pkt->out_buf != drv_state.data.ciphertext) {
memcpy(pkt->out_buf, drv_state.data.ciphertext,
ECB_AES_BLOCK_SIZE);
}
+
pkt->out_len = pkt->in_len;
+
return 0;
}
static int nrf_ecb_driver_init(const struct device *dev)
{
ARG_UNUSED(dev);
-
+#if defined(CONFIG_SOC_SERIES_NRF54LX)
+ /* Magic number in nRF54L15 OPS v0.5b page 251 8.7.2 EasyDMA */
+ #define NRF_VDMA_ATTRIBUTE_ECB 11
+
+ drv_state.data.in_job.p_buffer = (uint8_t *)&drv_state.data.cleartext;
+ drv_state.data.in_job.size = 0;
+ drv_state.data.in_job.attributes = NRF_VDMA_ATTRIBUTE_ECB;
+ drv_state.data.out_job.p_buffer = (uint8_t *)&drv_state.data.ciphertext;
+ drv_state.data.out_job.size = 0;
+ drv_state.data.out_job.attributes = NRF_VDMA_ATTRIBUTE_ECB;
+ nrf_ecb_in_ptr_set(NRF_ECB00, &drv_state.data.in_job);
+ nrf_ecb_out_ptr_set(NRF_ECB00, &drv_state.data.out_job);
+#else
nrf_ecb_data_pointer_set(NRF_ECB, &drv_state.data);
+#endif /* CONFIG_SOC_SERIES_NRF54LX */
drv_state.in_use = false;
return 0;
}
diff --git a/dts/common/nordic/nrf54l15.dtsi b/dts/common/nordic/nrf54l15.dtsi
index d3c0c551823..6a0e2a11fad 100644
--- a/dts/common/nordic/nrf54l15.dtsi
+++ b/dts/common/nordic/nrf54l15.dtsi
@@ -658,6 +658,13 @@
regulator-initial-mode = <NRF5X_REG_MODE_LDO>;
};
};
+
+ ecb00: ecb@47000 {
+ compatible = "nordic,nrf-ecb";
+ reg = <0x47000 0x1000>;
+ interrupts = <0x47 0x1>;
+ status = "okay";
+ };
};
rram_controller: rram-controller@5004b000 {
--
2.37.3.windows.1The nrf54l15.dtsi that I have seems different from the nrf54l15.dtsi you have.
I didn`t find regulator-initial-mode = <NRF5X_REG_MODE_LDO>; in it
Here is the file that I have
It's rename to nrf54l_05_10_15.dtsi in NCS v2.9.0.
It is worked. Thank you.