Hey folks,
i have to use the nrf9160 board to create a PoC for a project of our company. The main topic of the PoC is not important here because i cant even connect to an Azure IoT Hub.
I use the code of the nrf sdk sample with the Toolchain version 2.9 : sdk-nrf/samples/net/azure_iot_hub at main · nrfconnect/sdk-nrf
The code runs in a west workspace.
The LTE Connection works fine so far.
The board is able to build everything (it was hard to reach this point).
I use the Visual Studio extension to work with nrf.
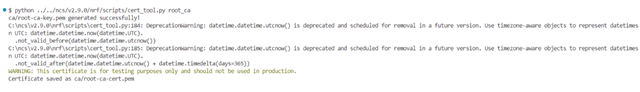
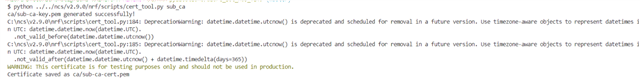
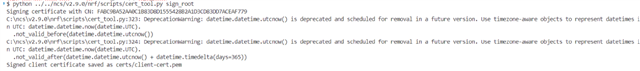
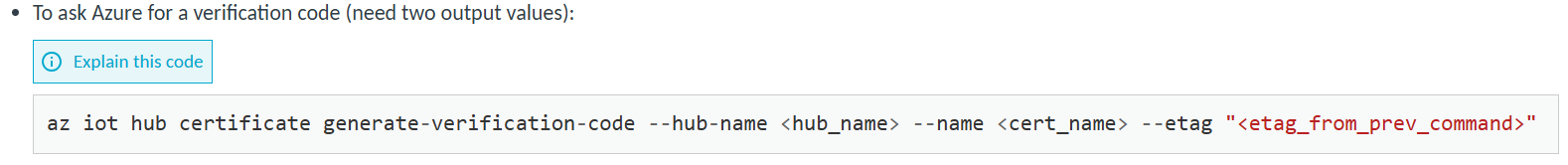
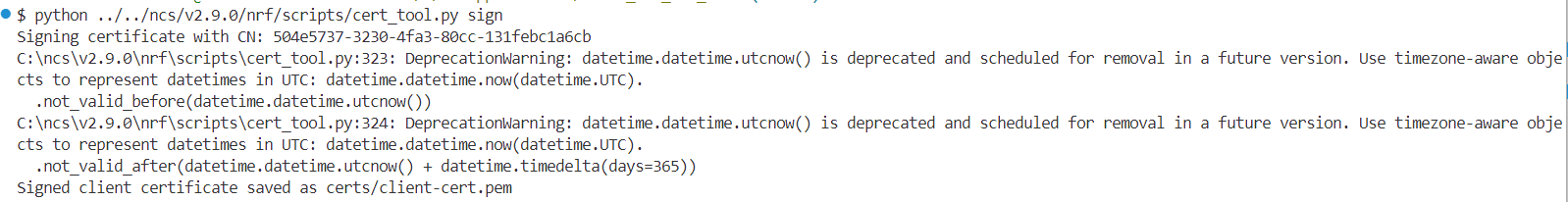
I know that the Problem is the Certificate, i followed the documentation to generate and provision the Certificates.
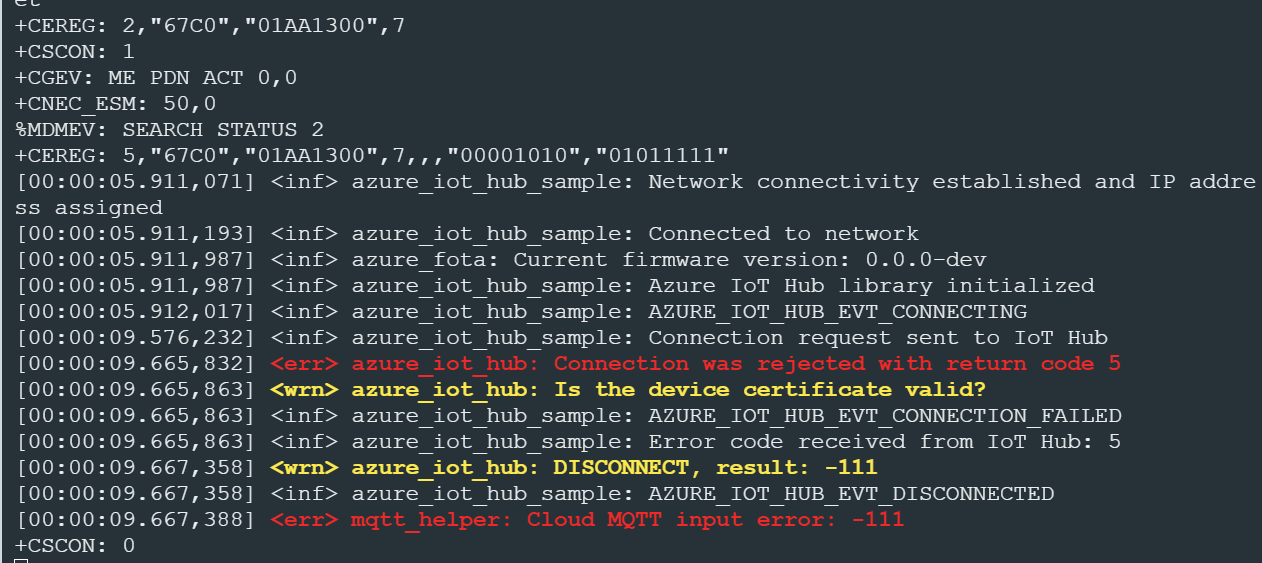
After everything is done i get this error =>
************************************************************************************************************************************
*** Booting nRF Connect SDK v2.9.0-7787b2649840 ***
*** Using Zephyr OS v3.7.99-1f8f3dc29142 ***
[00:00:00.253,784] <inf> azure_iot_hub_sample: Azure IoT Hub sample started
[00:00:00.253,845] <inf> azure_iot_hub_sample: Bringing network interface up and connecting to the network
[00:00:00.525,634] <inf> azure_iot_hub_sample: Device ID: XXXXXXXXX
[00:00:00.525,695] <inf> azure_iot_hub_sample: Host name: XXXXXXXXXXXXXXXXX
+CEREG: 2,"67C0","01AA1300",7
+CSCON: 1
+CGEV: ME PDN ACT 0,0
+CNEC_ESM: 50,0
%MDMEV: SEARCH STATUS 2
+CEREG: 5,"67C0","01AA1300",7,,,"00001010","01011111"
[00:00:05.561,889] <inf> azure_iot_hub_sample: Network connectivity established and IP address assigned
[00:00:05.562,011] <inf> azure_iot_hub_sample: Connected to network
[00:00:05.562,805] <inf> azure_fota: Current firmware version: 0.0.0-dev
[00:00:05.562,835] <inf> azure_iot_hub_sample: Azure IoT Hub library initialized
[00:00:05.562,835] <inf> azure_iot_hub_sample: AZURE_IOT_HUB_EVT_CONNECTING
[00:00:07.714,813] <inf> azure_iot_hub_sample: Connection request sent to IoT Hub
[00:00:07.798,614] <err> azure_iot_hub: Connection was rejected with return code 5
[00:00:07.798,645] <wrn> azure_iot_hub: Is the device certificate valid?
[00:00:07.798,645] <inf> azure_iot_hub_sample: AZURE_IOT_HUB_EVT_CONNECTION_FAILED
[00:00:07.798,675] <inf> azure_iot_hub_sample: Error code received from IoT Hub: 5
[00:00:07.799,896] <wrn> azure_iot_hub: DISCONNECT, result: -111
[00:00:07.799,926] <inf> azure_iot_hub_sample: AZURE_IOT_HUB_EVT_DISCONNECTED
[00:00:07.799,926] <err> mqtt_helper: Cloud MQTT input error: -111
+CEREG: 5,"67C0","01AA1302",7,,,"00001010","01011111"
********************************************************************************************************************************
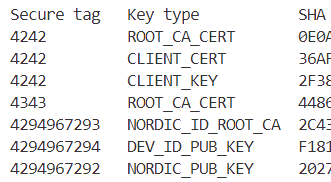
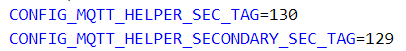
I made sure to set the
4242 ROOT_CA_CERT 0E0A61E2E78D28EEA66B15A9B10C1F4E5E8AD379FEA9131D02EC4A2473F9AB9C
4242 CLIENT_CERT 36AF6EF65D6EC7E800F407E7B7239301D3A359B81FC5475DED8851D87E5B6905
4242 CLIENT_KEY 2F38805AF55755FFEDFE71CC2D38C7AAA7AD20633BCA49E920796CEB768D5B8C
4343 ROOT_CA_CERT 44866CF6914A1AD1100147FA8432387FD5E63A5B5DFDD5A967A507AFEB78639B
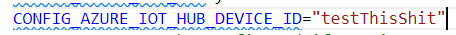
The Device i created in the IoT Hub uses x509_ca like mentioned in the documentation.
I even tried the self signed or Connection string but nothing worked.... i varied the creation of the Certificate in some ways but nothing led to success.
Does somebody know how to fix it ? I read some post in this Dev Zone but nothing helped.