I'm testing BLE secure communication with the nRF52840DK device and I have encountered a problem with bonds. I use modified example from BLE fundamental course, in which I added ability to determine if we connected to new or bonded client. The following steps will better describe my issue:
- Perform connection, pairing, and bonding with the nRF52840DK(Nordic_LBS).
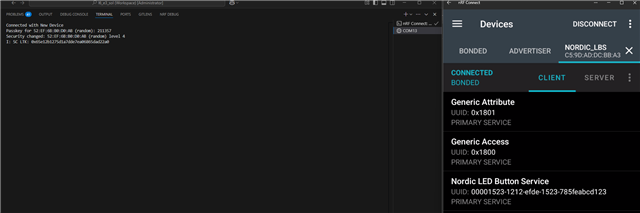
- Subscribe to Button characteristic notification(write to its CCCD 0x0001 value).
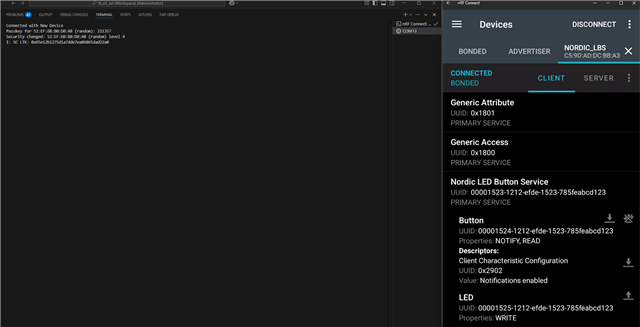
- Disconnect from nRF52840DK(Nordic_LBS).
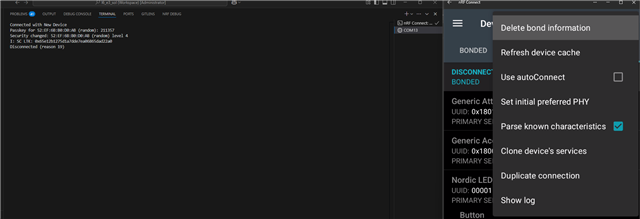
- Remove bonds on the client's side. (Bonds on nRF52840DK(Nordic_LBS) still present):
- Perform connection with the same nRF Connect client. As you can see, nRF52840DK(Nordic_LBS) still assume that it bonded with client.
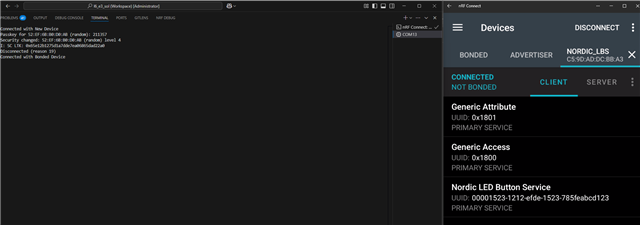
- Check Button characteristic CCCD value.
Expected result: 0x0000
Actual result: 0x0001
Same situation occurs even if in step 5 I perform connection, pairing, bonding again with the device. nRF connect logs and modified example attached.
nRF Connect, 2025-04-29 Nordic_LBS (C5:9D:AD:DC:BB:A3) V 10:54:20.015 Connecting to C5:9D:AD:DC:BB:A3... D 10:54:20.015 gatt = device.connectGatt(autoConnect = false, TRANSPORT_LE, preferred PHY = LE 1M) D 10:54:20.300 [Broadcast] Action received: android.bluetooth.device.action.ACL_CONNECTED D 10:54:20.301 [Callback] Connection state changed with status: 0 and new state: CONNECTED (2) I 10:54:20.301 Connected to C5:9D:AD:DC:BB:A3 V 10:54:20.302 Discovering services... D 10:54:20.302 gatt.discoverServices() D 10:54:20.425 [Callback] Services discovered with status: 0 I 10:54:20.425 Services discovered V 10:54:20.426 Generic Attribute (0x1801) - Service Changed [I] (0x2A05) Client Characteristic Configuration (0x2902) - Client Supported Features [R W] (0x2B29) - Database Hash [R] (0x2B2A) Generic Access (0x1800) - Device Name [R] (0x2A00) - Appearance [R] (0x2A01) - Peripheral Preferred Connection Parameters [R] (0x2A04) Nordic LED Button Service (00001523-1212-efde-1523-785feabcd123) - Button [N R] (00001524-1212-efde-1523-785feabcd123) Client Characteristic Configuration (0x2902) - LED [W] (00001525-1212-efde-1523-785feabcd123) D 10:54:20.426 gatt.setCharacteristicNotification(00002a05-0000-1000-8000-00805f9b34fb, true) D 10:54:20.427 gatt.setCharacteristicNotification(00001524-1212-efde-1523-785feabcd123, true) I 10:54:20.983 PHY updated (TX: LE 2M, RX: LE 2M) V 10:54:22.807 Starting pairing... D 10:54:22.807 device.createBond() D 10:54:22.872 [Broadcast] Action received: android.bluetooth.device.action.BOND_STATE_CHANGED, bond state changed to: BONDING (11) D 10:54:23.016 [Broadcast] Action received: android.bluetooth.device.extra.PAIRING_VARIANT, pairing variant: PIN I 10:54:25.497 Connection parameters updated (interval: 47.5ms, latency: 0, timeout: 420ms) D 10:54:40.213 [Broadcast] Action received: android.bluetooth.device.action.BOND_STATE_CHANGED, bond state changed to: BONDED (12) I 10:54:40.213 Device bonded V 10:55:08.990 Enabling notifications for 00001524-1212-efde-1523-785feabcd123 D 10:55:08.990 gatt.setCharacteristicNotification(00001524-1212-efde-1523-785feabcd123, true) D 10:55:08.992 gatt.writeDescriptor(00002902-0000-1000-8000-00805f9b34fb, value=0x0100) I 10:55:09.054 Data written to descr. 00002902-0000-1000-8000-00805f9b34fb, value: (0x) 01-00 A 10:55:09.054 "Notifications enabled" sent V 10:55:09.056 Notifications enabled for 00001524-1212-efde-1523-785feabcd123 V 10:55:23.185 Reading descriptor 00002902-0000-1000-8000-00805f9b34fb D 10:55:23.185 gatt.readDescriptor(00002902-0000-1000-8000-00805f9b34fb) I 10:55:23.256 Read Response received from descr. 00002902-0000-1000-8000-00805f9b34fb, value: (0x) 01-00 A 10:55:23.256 "Notifications enabled" received V 10:56:07.030 Disconnecting... D 10:56:07.030 gatt.disconnect() D 10:56:07.037 [Callback] Connection state changed with status: 0 and new state: DISCONNECTED (0) I 10:56:07.037 Disconnected D 10:56:08.067 [Broadcast] Action received: android.bluetooth.device.action.ACL_DISCONNECTED V 10:58:35.899 Removing bond information... D 10:58:35.899 device.removeBond() (hidden) D 10:58:35.983 [Broadcast] Action received: android.bluetooth.device.action.BOND_STATE_CHANGED, bond state changed to: NONE (10), reason: REMOVED (9) I 10:58:35.983 Bond information lost, reason: REMOVED (9) D 10:58:37.758 gatt.close() D 10:58:37.761 wait(200) V 10:58:37.964 Connecting to C5:9D:AD:DC:BB:A3... D 10:58:37.964 gatt = device.connectGatt(autoConnect = false, TRANSPORT_LE, preferred PHY = LE 1M) D 10:58:38.219 [Broadcast] Action received: android.bluetooth.device.action.ACL_CONNECTED D 10:58:38.235 [Callback] Connection state changed with status: 0 and new state: CONNECTED (2) I 10:58:38.235 Connected to C5:9D:AD:DC:BB:A3 V 10:58:38.254 Discovering services... D 10:58:38.254 gatt.discoverServices() D 10:58:38.346 [Callback] Services discovered with status: 0 I 10:58:38.346 Services discovered V 10:58:38.349 Generic Attribute (0x1801) - Service Changed [I] (0x2A05) Client Characteristic Configuration (0x2902) - Client Supported Features [R W] (0x2B29) - Database Hash [R] (0x2B2A) Generic Access (0x1800) - Device Name [R] (0x2A00) - Appearance [R] (0x2A01) - Peripheral Preferred Connection Parameters [R] (0x2A04) Nordic LED Button Service (00001523-1212-efde-1523-785feabcd123) - Button [N R] (00001524-1212-efde-1523-785feabcd123) Client Characteristic Configuration (0x2902) - LED [W] (00001525-1212-efde-1523-785feabcd123) D 10:58:38.349 gatt.setCharacteristicNotification(00002a05-0000-1000-8000-00805f9b34fb, true) D 10:58:38.355 gatt.setCharacteristicNotification(00001524-1212-efde-1523-785feabcd123, true) I 10:58:38.910 PHY updated (TX: LE 2M, RX: LE 2M) I 10:58:43.424 Connection parameters updated (interval: 47.5ms, latency: 0, timeout: 420ms) V 10:58:53.575 Reading descriptor 00002902-0000-1000-8000-00805f9b34fb D 10:58:53.575 gatt.readDescriptor(00002902-0000-1000-8000-00805f9b34fb) I 10:58:53.636 Read Response received from descr. 00002902-0000-1000-8000-00805f9b34fb, value: (0x) 01-00 A 10:58:53.636 "Notifications enabled" received D 10:58:53.639 gatt.setCharacteristicNotification(00001524-1212-efde-1523-785feabcd123, true) V 10:58:53.641 Notifications enabled for 00001524-1212-efde-1523-785feabcd123
Please advise if it is possible to handle that situation on the side. Or should it be handled on the client side and how?


