Hello Sir,
I am currently working with the boards:52840dk and ncs:2.9.1
Regarding the issue of failed mcuboot upgrade after writing the upgrade firmware using flash APIs, where the “zephyr.signed.bin” file is the one written to flash.
(The code in this routine has been modified.)
I first transferred the upgraded firmware to the memory via the serial port or other way.
Then, this is the process of writing to the flash using the flash API
while (offset < length)
{
size_t write_len = MIN(length - offset, CONFIG_IMG_BLOCK_BUF_SIZE); //Each time, write in blocks of size blocksize.
if (write_len < CONFIG_IMG_BLOCK_BUF_SIZE)
break;
ret = flash_img_buffered_write(&flash_ctx, &uart_rx_buf[offset],
write_len, false); //During the write process, the data in the last write buffer is less than the block size
if (ret != 0)
{
printk("Flash write failed at offset %zu: %d\n", offset, ret);
return ret;
}
offset += write_len;
}
ret = flash_img_buffered_write(&flash_ctx, NULL, 0, true); //flush The last written buffer
/*ret = flash_img_buffered_write(&flash_ctx, &uart_rx_buf[offset],
(length % 512), true);*/
if (ret != 0)
{
printk("Final flush failed: %d\n", ret);
return ret;
}
bytes_written = flash_img_bytes_written(&flash_ctx); //Buffer for the total number of bytes read and written
printk("Total bytes written: %zu\n", bytes_written);
if (bytes_written % UART_RX_MTU != 0) //Check if it has been fully written in
{
ret = boot_request_upgrade(BOOT_UPGRADE_PERMANENT); //If fully written, it will enter the DFU mode and start the update process
if (ret != 0)
{
printk("Failed to request upgrade: %d\n", ret);
return ret;
}
printk("Firmware update completed successfully!\n");
}
However, the update failed continuously. This is the error log reported by mcuboot.
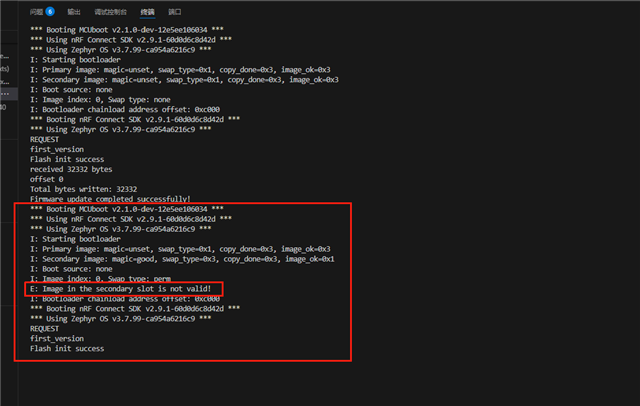
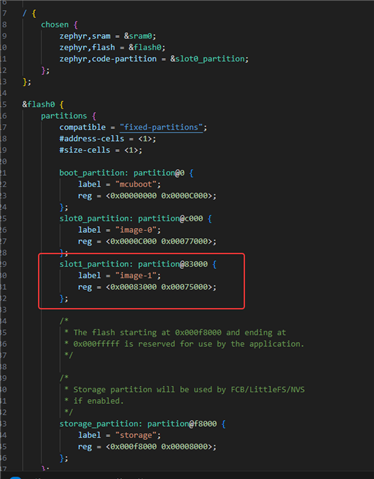
its display secondary slot is not vaild,then I dump flash data
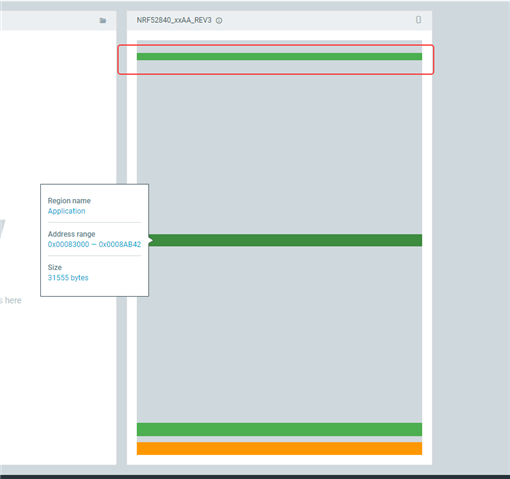
In Flash, the corresponding address contains the content I wrote, and the size and other details are also correct. Then, the part circled in red at the top should be the check bit of the swap_type located at the end of the secondary slot sector.
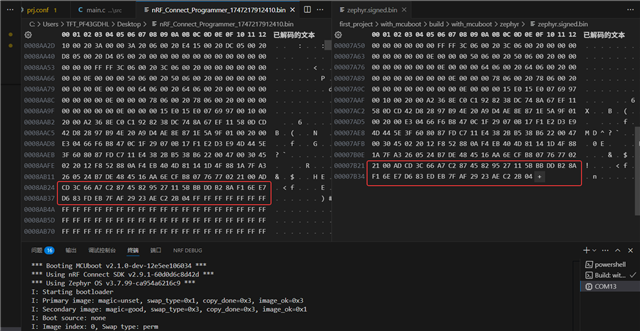
The specific content and the address where it is located have also been confirmed to be correct.
However, it was never able to be upgraded. Later, after debugging, it was found that the program failed during the hash verification process. it should be the verification of the TLV field. It is located at the end of the image, which is the part circled in the above picture.
Here's the problem: even though the contents in the flash are identical to the zephyr.signed.bin file, the upgrade still fails. Later, I dumped a Zephyr routine that can be upgraded successfully and checked the flash status before upgrading. I found that the TLV fields at the end of this routine's flash are different from the last 69 bytes of the zephyr.signed.bin in this routine.
I have found in many official and unofficial documents that this zephyr.signed.bin is used for DFU/OTA upgrades, and apart from this file, I haven't found any other new files that seem suitable for upgrading.
Then the remaining possibility is that since Zephyr uses west flash for burning, could it be that west flash modifies the signature? Or there might be other issues? What should I do next?
Please forgive my not-so-fluent English
Djangyond Kang,
Embedded Developer
Shenzhen Best of Best Holdings Co.,Ltd