Hi All,
In reference to my earlier ticket(https://devzone.nordicsemi.com/f/nordic-q-a/120183/question-on-immutable-bootloader-support-for-nrf54l15), I see SDK version 3.0 and latest version of SDK has experimental support of NSIB for nrf54l15.
Reference link: nRF Secure Immutable Bootloader
I am trying to build it as per the steps given in Enabling a bootloader chain using sysbuild and I am able to build the code. And able to see multiple hex files.
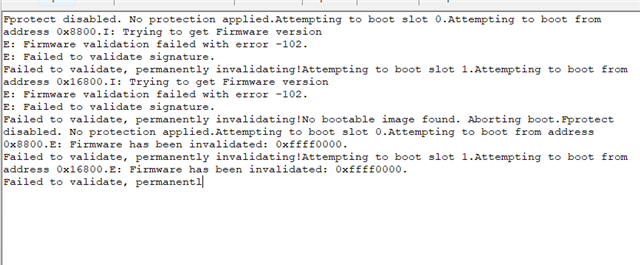
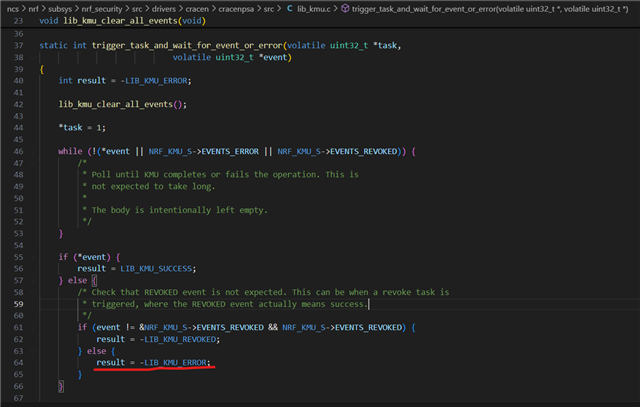
I tried to flash merged.hex and checked logs on console, however not able to see anything and looks like issue with the boot process. I am trying to debug it by enabling some logs.
Till the time, can anyone help on this, if I am missing in build, flash and test the code?
Thanks,
Nilesh