Hi,
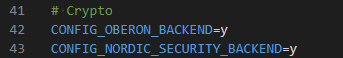
I'm trying to use MBEDTLS with MBEDTLS_USE_PSA_CRYPTO and CONFIG_PSA_CRYPTO_DRIVER_CC3XX activated.
Unfortunately I can't find a way to tell MBEDTLS that nRF9151 is not supporting SHA384.
When I execute mbedtls_ssl_setup(), psa_hash_setup() in ssl_tls.c always fails because the define MBEDTLS_MD_CAN_SHA384 is always activated
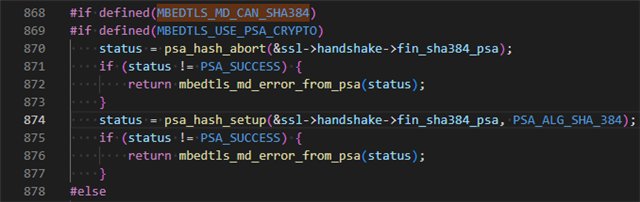
I tried to unset it in my project.conf by different way but nothing works :
- CONFIG_PSA_WANT_ALG_SHA_384=n (that willl be in the future the good way to do it but not supported yet even with SDK 3.0.1 - commit https://github.com/Mbed-TLS/mbedtls/pull/9171/commits still in development branche )
- CONFIG_MBEDTLS_MD_CAN_SHA384=n or CONFIG_MBEDTLS_SHA384_ALT=n => "error: ... is not directly user-configurable (has no prompt)"
- trying to set a custom config.h for MBEDTLS => warning: MBEDTLS_CFG_FILE (defined at .../v2.9.0/nrf/subsys/nrf_security/Kconfig:66, modules/mbedtls/Kconfig:58, modules/mbedtls/Kconfig:58) was assigned the value 'myconfig.h' but got the value 'nrf-config.h')
Any idea ?
Arnaud