I wanted a COAP Server running on nRF5340dk with DTLS and NS-Target without success.
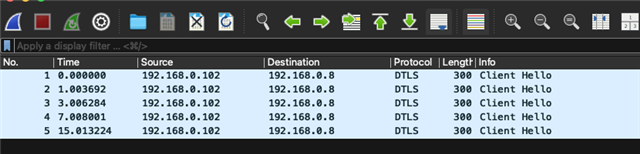
Whenever there is an attempt to connect to it from outside the app freezes, eg. shell becomes non responsive.
TL; DR
What I was able to do until now, was first do use the coap_server sample without DTLS and using the secure (standard) target.
Then I wanted first to use DTLS, which I was able to do, but some adaptions were required, because the current state of nordic sdk is a little bit behind (as of 10th June 2025 comparing SDK 3.0.2 to current zephyr main). The coap_server sample and stack have implemented support for DTLS, but after importing the few differences COAP+DTLS was running on the nRF, yet!.
But the final step is where I am stuck, switching from secure to non-secure target. I was able to switch some get rid of some mbed_tls options originally from the sample to use TLS/PSA instead. Here the official nrf TLS API sample helped to find options required to activate DTLS as well.
Long story short, I get to compile finally for NS-Target, but as described, when the connection is made, the application freezes. Does some one have seen similar behaviour, perhaps not explicitly COAP but in a Sense related to DTLS/Socket, or similar?
Here just more Details of my previous steps.
1) Ethernet Connection is working via additional spin/ethernet W5500 with the help of the existing W5500 ethernet driver, and device tree is adapted for using spi accordingly. But surely may work as well with rtt-driver as well.
2) Besides the required ethernet/ip config, the zephyr coap_server sample works practically out of the box, I adapted the config not to use IPv6 but IPv4 instead. Target here is currently secure (non ns)
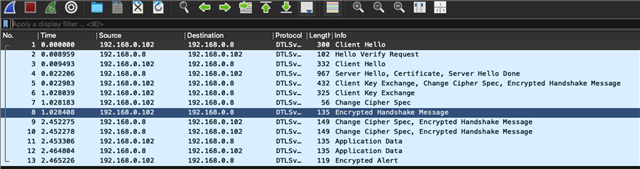
3) Enable DTLS support by including the respective DTLS overlay included with the coap_server sample, and voila DTLS works as well.
4) Switch to new build config for NS-Target, does not compile. So Adaptions are required, here is the updated overlay for NS-Target which finally compiles.
#Config to make the project compile for NS Target #The first part comes from original overlay CONFIG_NET_SAMPLE_COAPS_SERVICE=y # # Secure Socket CONFIG_NET_SOCKETS_SOCKOPT_TLS=y CONFIG_NET_SOCKETS_ENABLE_DTLS=y CONFIG_NET_SOCKETS_TLS_MAX_CLIENT_SESSION_COUNT=6 CONFIG_NET_SOCKETS_TLS_MAX_CONTEXTS=6 CONFIG_NET_SOCKETS_DTLS_TIMEOUT=30000 ##ORIGINAL Overlay for secure target adapted for ns # # TLS configuration #CONFIG_MBEDTLS_DEBUG=y #CONFIG_MBEDTLS=y # #CONFIG_MBEDTLS_BUILTIN=y # CONFIG_MBEDTLS_ENABLE_HEAP=y # CONFIG_MBEDTLS_HEAP_SIZE=60000 CONFIG_MBEDTLS_SSL_DTLS_CONNECTION_ID=y #CONFIG_MBEDTLS_SSL_MAX_CONTENT_LEN=2048 CONFIG_MBEDTLS_KEY_EXCHANGE_PSK_ENABLED=n # #Additional Changes (needed more stack) CONFIG_COAP_SERVER_STACK_SIZE=8192 ############ Imports from NRF TLS API SAMPLE # Networking CONFIG_NETWORKING=y CONFIG_NET_UDP=y CONFIG_NET_TCP=n CONFIG_NET_IPV6=n CONFIG_NET_IPV4=y CONFIG_NET_SOCKETS=y CONFIG_NET_TCP_ISN_RFC6528=n CONFIG_NET_CONFIG_SETTINGS=y CONFIG_NET_CONFIG_NEED_IPV6=n CONFIG_NET_CONFIG_NEED_IPV4=y CONFIG_POSIX_API=y CONFIG_NET_CONNECTION_MANAGER=n CONFIG_NET_CONTEXT_NET_PKT_POOL=y CONFIG_MBEDTLS_SSL_COOKIE_C=y # TLS networking CONFIG_ZVFS_OPEN_MAX=8 #CONFIG_NET_SOCKETS_TLS_MAX_CONTEXTS=6 CONFIG_NET_SOCKETS_TLS_MAX_CIPHERSUITES=16 # mbed TLS and security CONFIG_MBEDTLS_PK_C=y #CONFIG_MBEDTLS_ENABLE_HEAP=y #CONFIG_MBEDTLS_HEAP_SIZE=32768 CONFIG_MBEDTLS_SSL_IN_CONTENT_LEN=2304 CONFIG_MBEDTLS_SSL_OUT_CONTENT_LEN=2304 CONFIG_MBEDTLS_SSL_CLI_C=y CONFIG_MBEDTLS_TLS_LIBRARY=y CONFIG_MBEDTLS_X509_LIBRARY=y # NB: This list of PSA dependencies may be too long CONFIG_PSA_WANT_GENERATE_RANDOM=y CONFIG_PSA_WANT_KEY_TYPE_AES=y CONFIG_PSA_WANT_ALG_CCM=y CONFIG_PSA_WANT_ALG_GCM=y CONFIG_PSA_WANT_ALG_CHACHA20_POLY1305=y CONFIG_PSA_WANT_ALG_CMAC=y CONFIG_PSA_WANT_ALG_HMAC=y CONFIG_PSA_WANT_ALG_SHA_1=y CONFIG_PSA_WANT_ALG_SHA_224=y CONFIG_PSA_WANT_ALG_SHA_256=y CONFIG_PSA_WANT_ALG_SHA_384=y CONFIG_PSA_WANT_ALG_SHA_512=y CONFIG_PSA_WANT_ALG_ECB_NO_PADDING=y CONFIG_PSA_WANT_ALG_CBC_NO_PADDING=y CONFIG_PSA_WANT_ALG_CBC_PKCS7=y CONFIG_PSA_WANT_ALG_CTR=y CONFIG_PSA_WANT_ALG_HKDF=y CONFIG_PSA_WANT_ALG_TLS12_PRF=y CONFIG_PSA_WANT_ALG_ECDH=y CONFIG_PSA_WANT_ALG_ECDSA=y CONFIG_PSA_WANT_ALG_DETERMINISTIC_ECDSA=y CONFIG_PSA_WANT_ALG_JPAKE=y CONFIG_PSA_WANT_ECC_SECP_R1_256=y CONFIG_PSA_WANT_KEY_TYPE_ECC_KEY_PAIR_IMPORT=y CONFIG_PSA_WANT_KEY_TYPE_ECC_KEY_PAIR_EXPORT=y CONFIG_PSA_WANT_KEY_TYPE_ECC_KEY_PAIR_DERIVE=y CONFIG_PSA_WANT_KEY_TYPE_ECC_KEY_PAIR_GENERATE=y CONFIG_PSA_WANT_ALG_STREAM_CIPHER=y CONFIG_PSA_WANT_KEY_TYPE_CHACHA20=y CONFIG_PSA_WANT_ALG_TLS12_PSK_TO_MS=y #very important import from nrf tls api sample (nrf5340 specific overlay for ns-target) CONFIG_TFM_PROFILE_TYPE_NOT_SET=y CONFIG_NRF_ENABLE_ICACHE=n CONFIG_MBEDTLS_USE_PSA_CRYPTO=y CONFIG_MBEDTLS_PSA_CRYPTO_C=y CONFIG_PM_PARTITION_SIZE_TFM=0x60000
5) It seems that the COAP Client does not get a response at all to start a handshake, so I assume happens at connection level already, but can not tell what it is. So I think that the network stack does not even arrive to a step to check credentials at all.
Any suggestions, recommendations?