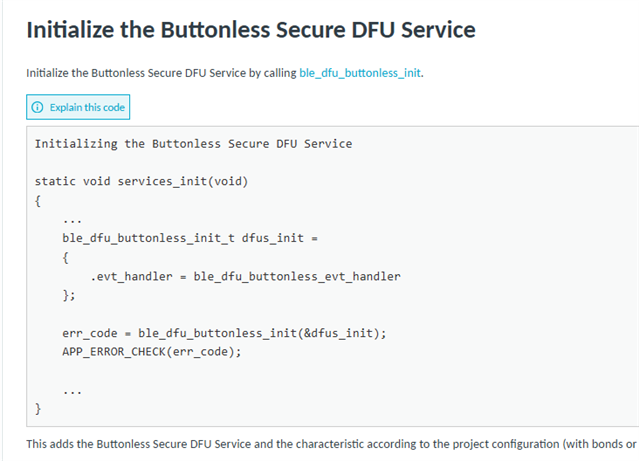
My product currently has DFU (Device Firmware Update) functionality enabled, but I want to allow firmware updates only after receiving a specific command via BLE. This is to prevent unauthorized sources from updating the device with incorrect firmware.
My current approach is to execute the following procedure upon receiving a specific BLE command:
If I don't write any value to gpregret, the system can reboot normally, and reading the value from gpregret works without any issues.
However, when I write a value to gpregret regardless of the method used—the system hangs after rebooting. Sometimes, continuous bootloader WDT messages appear.
I would like to ask if there’s a better approach to control whether DFU should be allowed.
In addition to the above issue, there's also the problem I mentioned earlier: disabling ble_dfu_buttonless_async_svci_init() causes BLE communication to stop working.
As for that issue, it seems that turning Bluetooth off and then back on again on the phone can resolve the problem—but this behavior is quite strange from a user’s perspective.
Thank you