Hi team.
Now i'm use soc nrf5340, and the ncs version 2.9.0.
I want to encrypt my external flash using QSPI.
I encountered some problems while using the nrf connect mobile app to perform the Bluetooth upgrade.
file postion : E:\Project\SDK\v2.9.0\bootloader\mcuboot\boot\zephyr\main.c
#ifdef CONFIG_MCUBOOT_ENC_EXT_FLASH
#define NONCE_CTX "test_string"
#include <hw_unique_key.h>
#include <nrfx_qspi.h>
static bool encryption_done = false;
int encrypt_external_flash(void)
{
if (encryption_done) {
printk("External flash already encrypted, skipping\n");
return NRFX_SUCCESS;
}
nrf_qspi_encryption_t encrypt_param = {0};
uint8_t label[3] = {0}; // Label used for both key and nonce
int ret = 0;
if (!hw_unique_key_are_any_written())
hw_unique_key_write_random();
// Derive the key
uint8_t key_context[16] = {0};
memcpy(key_context, CONFIG_BOARD, strlen(CONFIG_BOARD));
printk("Deriving keyyyyyyyyyyyyyyyyyyyyy with context: %s\n", key_context);
ret = hw_unique_key_derive_key(HUK_KEYSLOT_MEXT,
key_context, sizeof(key_context),
label, sizeof(label),
(uint8_t *)encrypt_param.key, sizeof(encrypt_param.key));
if (ret)
{
printk("derive board key error: %d\n", ret);
return ret;
}
// Derive the nonce
uint8_t nonce_context[32] = {0};
memcpy(nonce_context, NONCE_CTX, strlen(NONCE_CTX));
printk("Deriving nonceeeeeeeeeeeeeeeeee with context: %s\n", nonce_context);
ret = hw_unique_key_derive_key(HUK_KEYSLOT_MEXT,
nonce_context, sizeof(nonce_context),
label, sizeof(label),
(uint8_t *)encrypt_param.nonce, sizeof(encrypt_param.nonce));
if (ret)
{
printk("derive nonce ctx key error: %d\n", ret);
return ret;
}
// Perform encryption with DMA
ret = nrfx_qspi_dma_encrypt(&encrypt_param);
if (ret != NRFX_SUCCESS)
{
printk("nrfx_qspi_dma_encrypt error: %d\n", ret);
return ret;
}
// Perform encryption with XIP
ret = nrfx_qspi_xip_encrypt(&encrypt_param);
if (ret != NRFX_SUCCESS)
{
printk("nrfx_qspi_xip_encrypt error: %d\n", ret);
return ret;
}
MCUBOOT_WATCHDOG_FEED();
encryption_done = true;
printk("Set ext flash encryption done\n");
return NRFX_SUCCESS;
}
SYS_INIT(encrypt_external_flash, POST_KERNEL, 42);
#endif /*CONFIG_MCUBOOT_ENC_EXT_FLASH*/
file : prj.conf
CONFIG_NCS_SAMPLE_MCUMGR_BT_OTA_DFU=y
CONFIG_MCUMGR_MGMT_NOTIFICATION_HOOKS=y
CONFIG_CHIP_DFU_OVER_BT_SMP=y
file : sysbuild.conf
SB_CONFIG_PARTITION_MANAGER=y
SB_CONFIG_PM_EXTERNAL_FLASH_MCUBOOT_SECONDARY=y
file : sysbuild/mcuboot/prj.conf
CONFIG_NRF_SECURITY=y
CONFIG_MBEDTLS_RSA_C=y
CONFIG_MBEDTLS_LEGACY_CRYPTO_C=y
CONFIG_HW_UNIQUE_KEY=y
CONFIG_HW_UNIQUE_KEY_RANDOM=y
CONFIG_MCUBOOT_ENC_EXT_FLASH=y
When I disabled the operation of encrypting the external flash, my Bluetooth upgrade was successful.
However, when I enabled the encryption operation, the Bluetooth upgrade failed.
After printing and checking, it was found that the magic failed to match and the upgrade was unsuccessful.
E: Faled boot_set_next with code 3, for slot 1, with active slot 0 and confirm 0
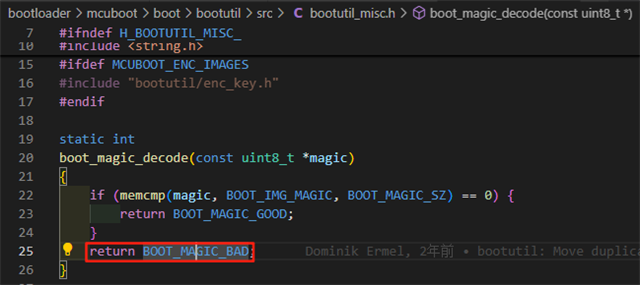
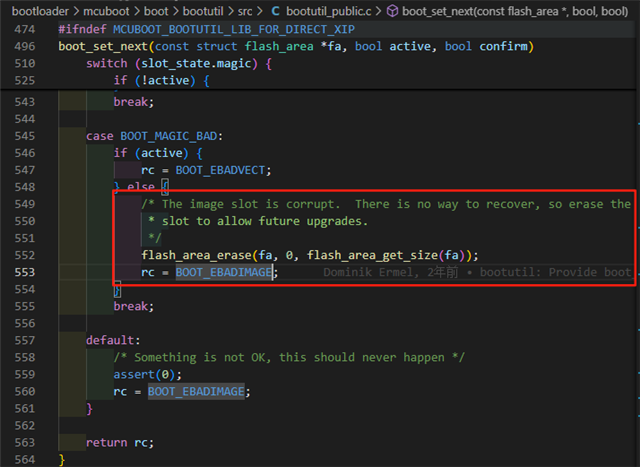
Will there be any problems with this encryption operation?
