Hello all, Nordic Team
i've a question regarding the format of the nonce used within CryptoCell Library v0.9.0.a
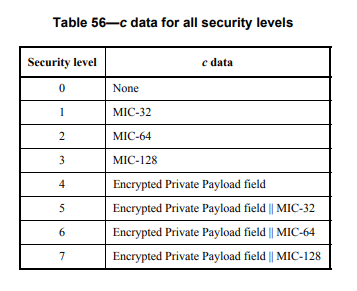
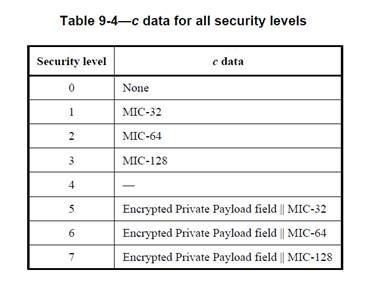
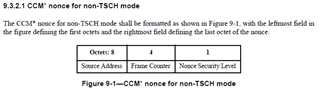
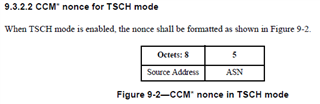
What i've learned so far is, that CRYS_AESCCMstar requires a nonce where the length of authentication tag can be derived. I don't find a standard describing that as mandatory. In ZigBee specification there is a sidenote about it but within IEEE802.15.4-2015 i can't find any relation.
I'm currently implementing some tests based on the test vectors given in the IEEE standard which are failing right now because of the above mention restriction.
As bjorn-spockeli mention in this thread:
there is a new version of the library in preparation. Are there any thoughts about this issue covered? Because if i'm using CRYS_AESCCM any nonce format is accepted. On the other hand encryption only is not support in CCM.
Are there other ways to access the cryptocell directly?
Best regards
Chris