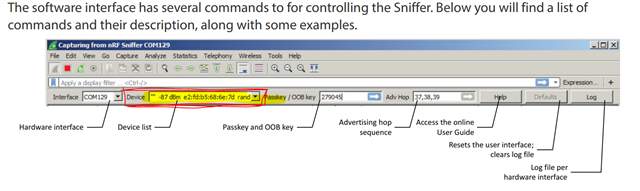
I am using nRF-Sniffer-v2.0.0.2 beta as seen here: https://www.nordicsemi.com/eng/nordic/Products/nRF-Sniffer/nRF-Sniffer-v2/65225 on a nRF52840 DK.
Wireshark Version: 2.4.6
MTU Size: 247
Connection Interval: 20 ms
Timeout: 4 sec
Peripheral application: Slightly modified Nordic BLE NUS example running on another nRF52840 DK.
Client application: nRF Connect running on an Android device.
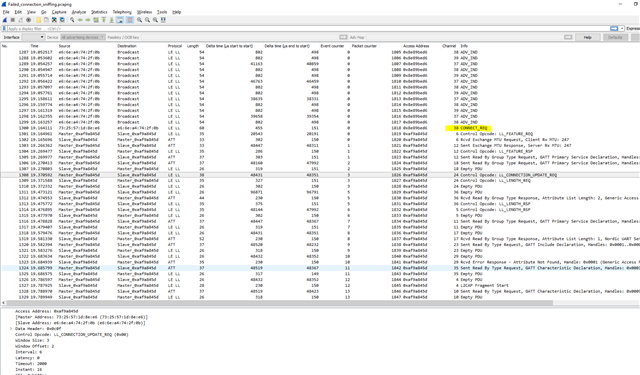
In short, after completing every troubleshooting step in the nRF_Sniffer_Users_Guide_v2.2, I am able to log and view advertising packets from my peripheral BLE device but cannot view packets after a connection has been established. I am connecting to my peripheral using nRF Connect on my Andoid phone. As soon as I connect, I no longer see any transmissions. From what I have read online, this is because Wireshark was not able to follow the complete connection process due to packet loss with seems to be the case according to the log below (Packet read timed out.).
This is what I have tried to remedy the problem:
1. Place the sniffer directly between the peripheral and client.(8 inches between each device).
2. Disable any other BLE devices in my environment.
3. Made sure that the ONLY J-Link driver installed on my machine is the one that came with the sniffer software (segger_jlink_v6_34b).
4. Made sure that the J-Link firmware on the development kit is v6.34b using JLinkConfig.exe and comparing the Emulator Firmware and Host Firmware dates.
5. Forced J-Link to use flow control with "sethwfc force" and unplugged all hardware and restarted all applications.
6. Tried installing J-Link drivers 6.16c which I read worked for some other users (This made no difference).
7. Tried disconnecting and reconnecting from/to the peripheral 10 times consecutively without luck.
I am a a loss as to what else to try. I need some way of sniffing packets that use DLE and large packet sizes. If the nRF51 devices can do this (which I don't think they can), I am willing to switch to other hardware or older software to get around this issue. See the log below and attached Wireshark log. Also note that once the connection is established, the peripheral is constantly pushing large packets of ~200 bytes to the client. This is seen on the nRF Connect Android app so I know packets are being sent. Besides, I would at least expect to see a bunch of empty PDU's. Also note that Notifications were enabled when these logs were captured.
nRF log reported in Wireshark:
------------------------------------------------------------
INFO: Log started at 10/25/18 00:37:28
INFO: args: ()
INFO: kwargs: {'callbacks': [('*', <bound method Sniffer.passOnNotification of <Sniffer(Thread-2, initial)>>)]}
INFO: board ID: 18
INFO: starting scan
INFO: starting scan
INFO: Sent key value to sniffer: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
INFO: Sent key value to sniffer: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
INFO: Sniffing device 0 - ""My Device - 2F0B""
INFO: Following "RAM Replay - 2F0B" e6:6e:a4:74:2f:0b random
INFO: Packet read timed out.
INFO: Packet read timed out.
INFO: Packet read timed out.
----------------------------------------------------------