Hi,
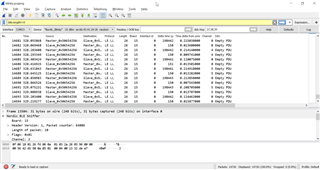
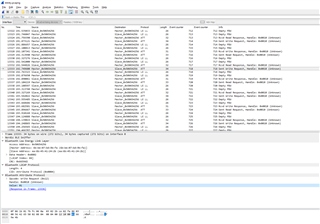
I am trying to understand Wireshark logs when sniffing packets. Please check the attachment. I have been reading about the description of advertising packets. Can you please check my logs and explain me which are the actual data packets? These logs were captured for BLE_UART example.uart_log.pcapng