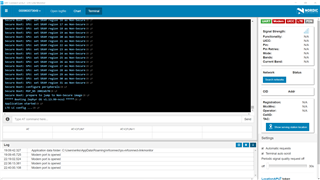
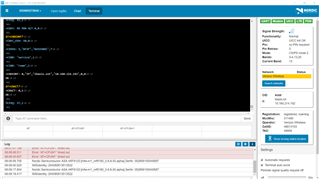
I am having trouble getting the nRF9160 DK to find a network running the Asset Tracker than came in the device. It appears to reset after 15 seconds of LED 3 blinking. I can connect the LTE Link Monitor and watch it do that. Secure Boot boots to Zephyr and then about 15 seconds approx later it says it failed (nrf_cloud_connect failed: 60) and starts all over again. Really difficult and unreliable to get to the state of LED 3 and LED 4 both blinking. Sometimes just stops with LED 3 lit solid.
I have had it connected a number of times, but not reliably. The SIM is registered. This is making it difficult to get the things linked to my nRF Cloud account when I am having trouble even getting to the pattern entry portion of setting this up.
Is there an issue with the asset tracker that came in the device such that it won't connect? Something else I might have going on? I have not loaded anything different into the DK than what it came with.
Thanks,
Erik