Hello,
I'm attempting to connect the nRF9160 DK to our AWS IoT account. I've been following the information in this question: https://devzone.nordicsemi.com/f/nordic-q-a/44528/switch-cloud-endpoint-from-nordic-aws-to-our-own-aws-account but I'm having an issue establishing the connection.
So far I have been able to call the certificates from a replica of 'certificates.h' and flash these onto the nRF91 using the nrf_inbuilt_key commands and have been able to establish a broker connection but receive a time out error when connecting to AWS with MQTT. I am currently modifying mqtt_simple to acheve this connection.
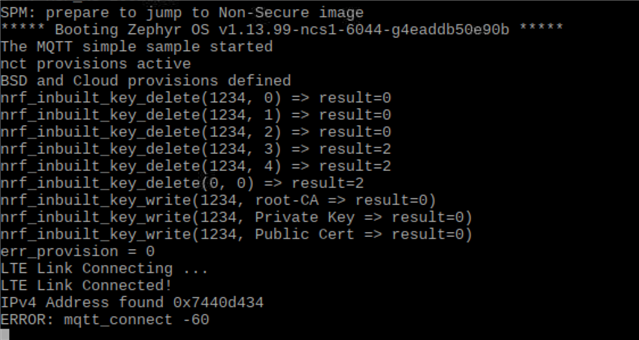
So far I have updated 'pj.conf' with:
# General config CONFIG_TEST_RANDOM_GENERATOR=y # Networking CONFIG_NETWORKING=y CONFIG_NET_SOCKETS_OFFLOAD=y CONFIG_NET_SOCKETS=y CONFIG_NET_SOCKETS_POSIX_NAMES=y # LTE link control CONFIG_LTE_LINK_CONTROL=y CONFIG_LTE_AUTO_INIT_AND_CONNECT=n CONFIG_NRF_CLOUD_PROVISION_CERTIFICATES=y # BSD library CONFIG_BSD_LIBRARY=y # AT Host CONFIG_UART_INTERRUPT_DRIVEN=y CONFIG_AT_HOST_LIBRARY=y # MQTT CONFIG_MQTT_LIB=y CONFIG_MQTT_LIB_TLS=y # Appliaction CONFIG_MQTT_PUB_TOPIC="my/publish/topic" CONFIG_MQTT_SUB_TOPIC="my/subscribe/topic" CONFIG_MQTT_CLIENT_ID="MQTT_TEST" CONFIG_MQTT_BROKER_HOSTNAME="xxxxxxxxxxx.iot.eu-west-1.amazonaws.com" (redacted) CONFIG_MQTT_BROKER_PORT=8883 CONFIG_NRF_CLOUD_SEC_TAG=1234 # Main thread CONFIG_MAIN_THREAD_PRIORITY=7 CONFIG_MAIN_STACK_SIZE=4096 CONFIG_HEAP_MEM_POOL_SIZE=1024
I have added the following additional functions to mqtt_simple:
#include "certificates.h"
#define NRF_CLOUD_HOSTNAME CONFIG_MQTT_BROKER_HOSTNAME
#define NRF_CLOUD_SEC_TAG CONFIG_NRF_CLOUD_SEC_TAG
static struct nct {
struct mqtt_sec_config tls_config;
struct mqtt_client client;
struct sockaddr_storage broker;
struct mqtt_utf8 dc_tx_endp;
struct mqtt_utf8 dc_rx_endp;
u32_t message_id;
} nct;
static void client_init(struct mqtt_client *client)
{
mqtt_client_init(client);
broker_init();
/* MQTT client configuration */
client->broker = &broker;
client->evt_cb = mqtt_evt_handler;
client->client_id.utf8 = (u8_t *)CONFIG_MQTT_CLIENT_ID;
client->client_id.size = strlen(CONFIG_MQTT_CLIENT_ID);
client->password = NULL;
client->user_name = NULL;
client->protocol_version = MQTT_VERSION_3_1_1;
/* MQTT buffers configuration */
client->rx_buf = rx_buffer;
client->rx_buf_size = sizeof(rx_buffer);
client->tx_buf = tx_buffer;
client->tx_buf_size = sizeof(tx_buffer);
nct.client.transport.type = MQTT_TRANSPORT_SECURE;
struct mqtt_sec_config *tls_config = &nct.client.transport.tls.config;
memcpy(tls_config, &nct.tls_config, sizeof(struct mqtt_sec_config));
}
static int nct_provision(void)
{
printk("nct provisions active\n");
static sec_tag_t sec_tag_list[] = {NRF_CLOUD_SEC_TAG};
nct.tls_config.peer_verify = 2;
nct.tls_config.cipher_count = 0;
nct.tls_config.cipher_list = NULL;
nct.tls_config.sec_tag_count = ARRAY_SIZE(sec_tag_list);
nct.tls_config.sec_tag_list = sec_tag_list;
nct.tls_config.hostname = CONFIG_MQTT_BROKER_HOSTNAME;
int err;
printk("BSD and Cloud provisions defined\n");
/* Delete certificates */
nrf_sec_tag_t sec_tag = NRF_CLOUD_SEC_TAG;
for (nrf_key_mgnt_cred_type_t type = 0; type < 5; type++) {
err = nrf_inbuilt_key_delete(sec_tag, type);
printk("nrf_inbuilt_key_delete(%d, %d) => result=%d\n",
sec_tag, type, err);
}
err = nrf_inbuilt_key_delete(0,0);
printk("nrf_inbuilt_key_delete(0, 0) => result=%d\n",
err);
/* Provision CA Certificate. */
err = nrf_inbuilt_key_write(NRF_CLOUD_SEC_TAG,
NRF_KEY_MGMT_CRED_TYPE_CA_CHAIN,
NRF_CLOUD_CA_CERTIFICATE,
strlen(NRF_CLOUD_CA_CERTIFICATE));
printk("nrf_inbuilt_key_write(%d, root-CA => result=%d)\n",
NRF_CLOUD_SEC_TAG, err);
if (err) {
printk("NRF_CLOUD_CA_CERTIFICATE err: %d", err);
return err;
}
/* Provision Private Certificate. */
err = nrf_inbuilt_key_write(
NRF_CLOUD_SEC_TAG,
NRF_KEY_MGMT_CRED_TYPE_PRIVATE_CERT,
NRF_CLOUD_CLIENT_PRIVATE_KEY,
strlen(NRF_CLOUD_CLIENT_PRIVATE_KEY));
printk("nrf_inbuilt_key_write(%d, Private Key => result=%d)\n",
NRF_CLOUD_SEC_TAG, err);
if (err) {
printk("NRF_CLOUD_CLIENT_PRIVATE_KEY err: %d", err);
return err;
}
/* Provision Public Certificate. */
err = nrf_inbuilt_key_write(
NRF_CLOUD_SEC_TAG,
NRF_KEY_MGMT_CRED_TYPE_PUBLIC_CERT,
NRF_CLOUD_CLIENT_PUBLIC_CERTIFICATE,
strlen(NRF_CLOUD_CLIENT_PUBLIC_CERTIFICATE));
printk("nrf_inbuilt_key_write(%d, Public Cert => result=%d)\n",
NRF_CLOUD_SEC_TAG, err);
if (err) {
printk("NRF_CLOUD_CLIENT_PUBLIC_CERTIFICATE err: %d",
err);
return err;
}
return 0;
}
void main(void)
{
int err;
int err_provision;
printk("The MQTT simple sample started\n");
err_provision = nct_provision();
if (err_provision != 0) {
printk("ERROR: nct_provision failure %d\n", err_provision);
return;
}
printk("err_provision = %d\n", err_provision);
modem_configure();
client_init(&client);
I have changed the following in Kconfig:
menu "MQTT simple sample" config MQTT_PUB_TOPIC string "MQTT publish topic" default "my/publish/topic" config MQTT_SUB_TOPIC string "MQTT subscribe topic" default "my/subscribe/topic" config MQTT_CLIENT_ID string "MQTT Client ID" default "MQTT_TEST" config MQTT_BROKER_HOSTNAME string "MQTT broker hostname" default "xxxxxxxxx.iot.eu-west-1.amazonaws.com" (redacted) config MQTT_BROKER_PORT int "MQTT broker port" default 8883 config MQTT_MESSAGE_BUFFER_SIZE int "" default 128 config MQTT_PAYLOAD_BUFFER_SIZE int "" default 128 config NRF_CLOUD_SEC_TAG int "" default 1234
Finally, the certs are inside certificates.h:
/* * Copyright (c) 2018 Nordic Semiconductor ASA * * SPDX-License-Identifier: BSD-5-Clause-Nordic */ #define NRF_CLOUD_CLIENT_ID "MQTT_TEST" #define NRF_CLOUD_CLIENT_PRIVATE_KEY \ "-----BEGIN RSA PRIVATE KEY-----\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "-----END RSA PRIVATE KEY-----\r\n" #define NRF_CLOUD_CLIENT_PUBLIC_CERTIFICATE \ "-----BEGIN CERTIFICATE-----\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "-----END CERTIFICATE-----\r\n" #define NRF_CLOUD_CA_CERTIFICATE \ "-----BEGIN CERTIFICATE-----\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "xxxxxxx\r\n" \ "-----END CERTIFICATE-----\r\n"
I'm not sure what is still left to change in order to make the connection to AWS.


