I've got Wireshark running with nRF Sniffer, but it is not really working for me.
I'm using a PCA10040 board as the sniffer hardware.
I'm running on a Mac with MacOS 10.14.4.
I'm running Python 2.7.10 and I installed PySerial 2.7.
I downloaded nrfsniffer200beta312oct20181c2a221.zip.
I installed the hex file for PCA10040 onto the board.
I installed the nRF profile into Wireshark and installed the python scripts into the extcap folder.
Note that I first installed Wireshark 3.0.2 and then downgraded to 2.6.9, which did not affect my issue.
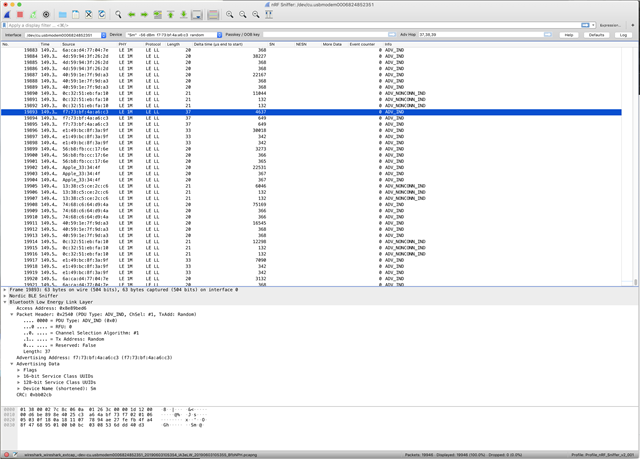
When I run Wireshark, I can select the nRF sniffer profile and I can select the interface to my sniffer board. I see all of the advertising data for all devices, but when I select a specific device from the Device popup menu, it does not affect the output. I still see all of the advertising data. If I select my device and connect to it from my iPad then I see the advertising stop for my device, but I continue to see the advertising packet for all of the other devices in my area. Also, I only see advertising data. It does not show any other packet types from my device.
Here is the log window contents after selecting my device.
INFO: Log started at Fri May 31 15:37:30 2019
INFO: args: ()
INFO: kwargs: {'callbacks': [('*', <bound method Sniffer.passOnNotification of <Sniffer(Thread-2, initial)>>)]}
INFO: board ID (random): 156
INFO: starting scan
INFO: starting scan
INFO: Sent key value to sniffer: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
INFO: Sent key value to sniffer: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
INFO: Sniffing device 13 - ""Sm""
INFO: Following "Sm" f7:73:bf:4a:a6:c3 random
It says it is following my device, but it is still following all devices.
Any help is appreciated.