Hi,
I am fiddling with this example from the SDK:
infocenter.nordicsemi.com/in...cp=5_1_4_3_1_2
In this example, there is a test regarding key derivation as:
static void uc_key_derivation(void)
{
optiga_lib_status_t optiga_lib_status;
uint8_t info[100] = { 0 };
uint16_t info_len = 100;
uint16_t oid = 0xF1D0;
uint8_t shared_secret[64] = { 0 };
// Check if key derivation is supported (OPTIGA Trust X after version 1.20.1048)
optiga_lib_status = optiga_util_read_data(0xE0C2, 0, info, &info_len);
DEMO_OPTIGA_ERROR_CHECK(optiga_lib_status);
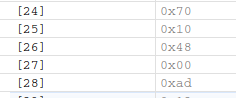
if (info[25] == 0x10 && info[26] == 0x48) // !!!! THIS CONDITION RETURNS TRUE
{
NRF_LOG_INFO("Key derivation not supported!\r\n");
NRF_LOG_FLUSH();
return;
}
As I understand, it checks the fw version of the Optiga TrustX module for whether key derivation is supported or not. According to the reply of the TrustX device, the function returns with 'Key derivation not supported!' message.
The thing is that, in the datasheet (revision 2.6), it clearly says TrustX supports key derivation in the first page.
"Crypto ToolBox with ECC NIST P256, P384, SHA-256 (sign, verify, key generation, ECDH, key derivation)"
I appreciate if anybody has any experience with Optiga Trust X, and share it here. I wonder if it is possible to use key derivation with Optiga TrustX or not, if possible, then how. Product page is here
Best regards,
Vedat