Environment
- DK 0.8.2 in which SB44 is cut, and P1 and P2 are connected
- firmware v1.0.0
- program : asset_tracker
- SIM: iBasis
Before updating firmware, asset_tracker worked fine.
However, after updating, LED3 is always blinking and LED4 is off.
What I do is to write the program to DK, push reset button, and wait for more than 5 min.
at_client program and LTE Link Monitor works out with v1.0.0.
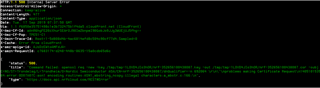
this is log
SPM: NS image at 0xc000 SPM: NS MSP at 0x2002aa00 SPM: NS reset vector at 0x142f1 SPM: prepare to jump to Non-Secure image. ***** Booting Zephyr OS v1.14.99-ncs2-rc3 ***** Asset tracker started Connecting to LTE network. This may take several minutes. Connected to LTE network
Any idea to solve this?