Hi !
I am working on SDK 15.2 and on a NRF52832.
The others devices I will interact with are on BLE 4, so I can use only Legacy Connection mode for security.
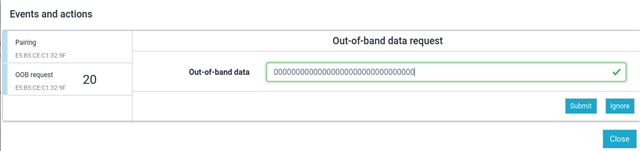
I would like to use Out of Band mode, with a pre shared key stored on my device. The other device, a BLE Gateway, will have a file with this key stored too.
First, I would like to know if there are examples to do that.
Second, i would like to know if it is possible to modify the value of the key and keep its value even if we switch off the device.
Thanks,